This post was authored by Mike McGhee, Director TMM and Rishi Thaper, Principal Product Manager
Implementing effective access control for unstructured data is a challenging and complex task. A typical mid- to large-size enterprise organization has a massive amount of unstructured data within a dynamic environment.
Unstructured data is growing at an unprecedented pace, and to make matters worse, maintaining permissions on repositories of unstructured data is becoming even more challenging.
There can be thousands of shares in an organization, hundreds of thousands of folders and numerous control points, thousands of users and groups, and nested security groups. Every day, people change roles or leave organizations, projects & applications are initiated in different parts of organizations, requiring permission changes for various employees and contractors.
New requests for granting and revoking access come daily to IT teams as well as identity and access managers, which can make access impossible to control.
Silos between the IT and identity access management (IAM) processes further limit unified access and visibility across these groups. Active Directory (AD) security groups are modified and created regularly, and sometimes IT admins or owners change permissions on the file system’s access control lists (ACLs), adding another layer of complexity. Analyzing access risks at scale and evaluating and bubbling up the most significant security threats is a massive challenge.
Exposure Risk
One of the most significant challenges with access control is exposure risk. Exposure risk based on overly broad user access permissions can lead to people in an organization getting access to non-public information. The question is: How does the data, which initially had controlled access, get exposed? To answer that, you need to understand the access provisioning process.
In most cases, an IT admin will configure access on the top-level folder as per business requirements and provide access to different individuals using security groups and making changes to the ACLs. These groups may be nested, containing other security groups, and all the members get access to the data as per the permissions set in the ACL.
Complexity arises as the IAM admin, who is involved in the upkeep of access management from a directory services perspective, updates a security group to include a broad access group at a business request without knowing the repercussions of the change.
While access to other data might be a business requirement at the time, it unexpectedly opens access to this specific folder without the IAM admin having any visibility into the repercussions, causing exposure to potentially sensitive data. This can lead to significant risks from malicious insiders, disgruntled employees, hackers, and even ransomware. Global groups like everyone or authenticated users or even broad organizational groups should only have access to public data.
Unintended Access
A second risk and challenge that organizations face is the issue of unintended access. Over time, changes to security groups may open access to sensitive information to unintended users like contractors. This can include access to a customer’s and employee’s personal data. Misconfigurations and limited visibility into who has access to the data can have grave consequences, such as data leaks or catastrophic breaches.
Ensure Best Practices Access Provisioning
A third challenge for organizations is ensuring best practices around access provisioning and maintenance. Violations often occur, leading to more significant headaches in analyzing and remedying permissions.
One such example is broken inheritance. Generally, organizations would like to assign permissions to a top folder based on business requirements and allow propagation in the hierarchy. They can manage security effectively if the access is propagated or restricted, but it can cause issues if data becomes overly permissive in the file system hierarchy.
Here’s an example: A file system owner changes permissions to a specific folder and adds access for another group and a user. This will open up access to many more users and can be a violation of the organization’s best practices and a risky change overall.
Excessive Access to Individuals
A fourth challenge organizations face is excessive access to individuals. Access should depend on business needs and data content. More often than not, individuals get excessive effective permissions to data due to memberships in multiple security groups and group nesting.
If their business roles require them to read and review certain data, they inadvertently get modify or full control access. Having visibility into effective access and user entitlements can ensure the timely resolution of such access issues, thus reducing risk.
Remediation
Lastly, organizations require effective remediation in accordance with business requirements, while ensuring no disruption to operations. Once organizations get visibility into access risks, they must understand how to remediate access.
Based on an organization’s maturity, they may involve business units in managing access controls. Once business units provide inputs on permissions changes, the real work to analyze how to remediate begins.
Remediation requires determining where to make changes in the file system or security group and what-if analysis of the proposed change. Understanding remediation points for permissions is a complex but essential job for admins in any organization to reduce risk without disrupting legitimate access and business operations.
Nutanix Data Lens Permissions Monitoring
Nutanix Data Lens has always captured audit trails, which help you understand the operations occurring in an environment, including permission changes. But as seen by the aforementioned challenges, organizations must understand more than whether a permission change occurred. They need insights into exactly what changed and whether the changes increase risk to the system.
Nutanix Data Lens permissions monitoring helps you understand the current permissions in Nutanix Files environments, the risk those permissions present, and any specific permission changes. Nutanix Data Lens also provides custom reporting across these capabilities.
Permission Changes
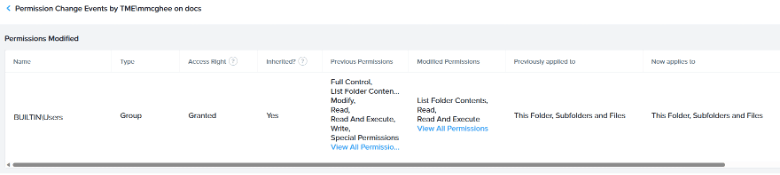
With Nutanix Data Lens, you can view the full history of permission change events and examine specific events to answer questions like:
- When did the change occur?
- Who made the change?
- On which share did the change occur?
- Was a permission added or removed?
- Is there inheritance with the change?
- What specific permissions were impacted?
Permissions Visibility
Along with seeing permission changes, you can directly view the end-to-end permissions in your environment. Nutanix Data Lens provides views and search capabilities from the share and directory perspective or from the user or group.
From the share and directory view, you can start from the share level and drill down into folders to see the share risk score, folder owner, total size, and total file count for each entity.
You can then choose to see which users have access to that share or folder, including the effective permissions and deeper NTFS permissions.
The users and groups page displays effective permissions from the user or group to the shares and folders on the file server. You can easily search for a specific user or group and see all the shares and folders to which they have access. You can also see Active Directory user membership for discovered groups and group membership for discovered users.

Risk Score
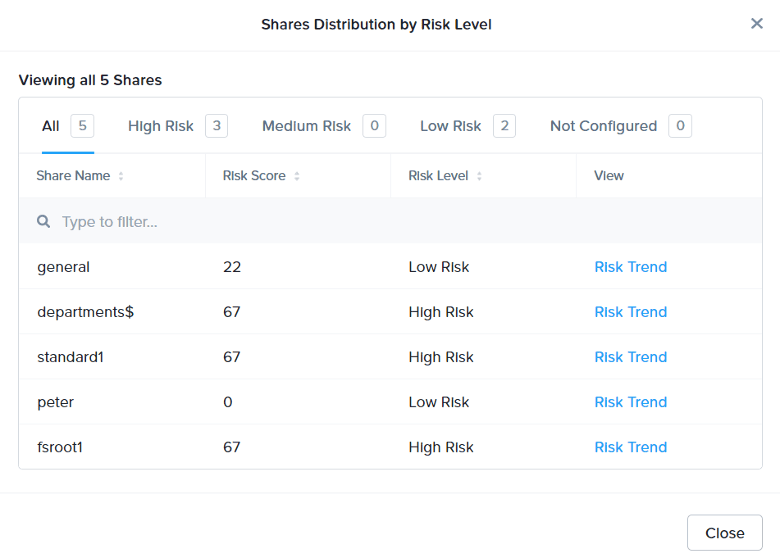
Nutanix Data Lens further helps you understand your permissions landscape with a configurable risk score. The risk score starts with defining your risk profile. A risk profile consists of predefined risk factors such as folders with full control, modify actions, open access, without admin access, and control points (non-inherited permissions.) You define whether each risk factor has a low-, medium-, or high-risk impact. You can also define a threshold as a percentage or number of folders to measure the risk.

Finally, you decide which shares use the risk profile. Nutanix Data Lens calculates the risk score for each share, which is a value from 0 to 100. You can then compare the risk score between specific shares and folders to gain an initial understanding of your high-risk shares to focus on for potential remediation.
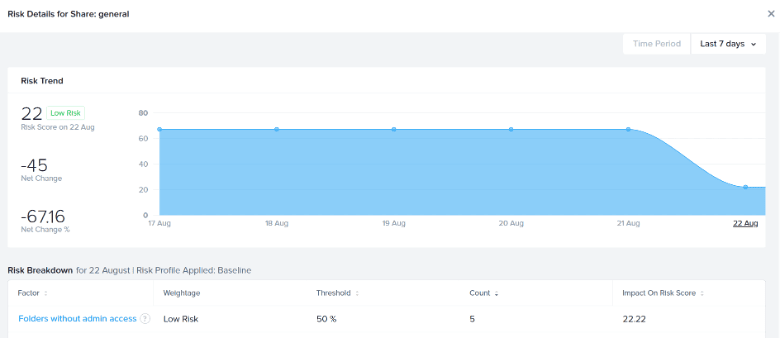
Nutanix Data Lens tracks changes to your risk score as permissions and group memberships are modified, creating a risk trend. The risk trend helps you understand whether risks are increasing or decreasing over time as changes occur.
Permissions Dashboard
Nutanix Data Lens consolidates much of this information into a dashboard that gives you an overview of:
- Distribution of shares based on your defined risk profile.
- Number of folders with permissions based on different attributes, like folders with full control or folders without admin access, that contribute to your risk score.
- Number of permission-change events over a selected period.
- Environment recommendations, such as alerting if shares don’t have a risk profile applied or shares that have high threshold counts.
- Permission denials over a selected period.
- Overall footprint, including number of folders, users, and groups and the total size of all files.
The Nutanix Data Lens reporting page includes templates to extract the information you see on the permissions dashboard and elsewhere. For example, you can use the reporting function to export a list of all the folders a given user or group has access to for further analysis or for sharing with other groups.
Conclusion
With native permissions monitoring, Nutanix Data Lens helps you analyze your access risks at scale for your Nutanix Unified Storage. It helps you address the challenges of data exposure, unintended or excessive access, and broken inheritance. As file system permissions or user and group membership information change over time, the configurable risk score helps you detect unintended events.
Visibility into these events helps you limit your exposure to data leaks from malicious insiders, hackers, and ransomware attacks. These are just some of the ways that Nutanix Data Lens gives you an active defense for your unstructured data. We encourage you to visit the Nutanix Data Lens web page to learn more.
© 2024 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.





