Nutanix customers can set up a secure Virtual Private Network (VPN) connection to connect their on-prem datacenter or remote user device to Xi Cloud Services using a Palo Alto Networks VM-Series firewall. A VPN solution enables secure communication between your on-prem Prism Central instance and the production Virtual Private Cloud (VPC) in Xi Cloud Services for replication, and allows users to access the applications running in the cloud.
This blog will cover the following topics:
- Internet traffic path from a VM running on Xi for a single legged vPAN design
- Configuring policies and rerouting Internet/VM traffic from a Palo Alto Networks VM-Series virtual appliance on Xi to an on-prem Palo Alto Networks firewall
Design
Nutanix recommends the following design for the Palo Alto Networks VM-Series virtual appliance:
A single-legged design with one inside interface and one management interface. The management interface can have a public IP assigned to it if you need to manage the firewall by using a public IP. The firewall can also be managed using an internal IP, if that subnet is reachable from the on-prem side through an existing VPN tunnel.
In this design, instead of using zones, you can use IP policies in the firewall itself to control the traffic.
NOTE: Nutanix does not recommend a two-legged design with zones.
Advantages of using single-legged design:
- It is easier to configure due to the simple design. Keep it simple and away from complex configurations for your firewall.
- Avoid issues with routing loops in this design.
What are you missing from a two-legged design?
- You cannot use zones on Palo Alto Networks VM-Series virtual appliance due to a single interface and would need to manage everything using IP policies.
Nutanix has a construct of virtual routers in Xi where Nutanix host the gateways of all the subnets in the VPCs. When traffic routes between two different subnets on the Xi side, it traverses through this virtual router and is forwarded to the desired next hop by the virtual router.
The traffic from a failed-over VM or a live VM running on Xi through the VM-Series will follow different paths when traversing through the interfaces as shown below.
Internet Traffic Path for a Single Legged Design (Inside and Management Interface)
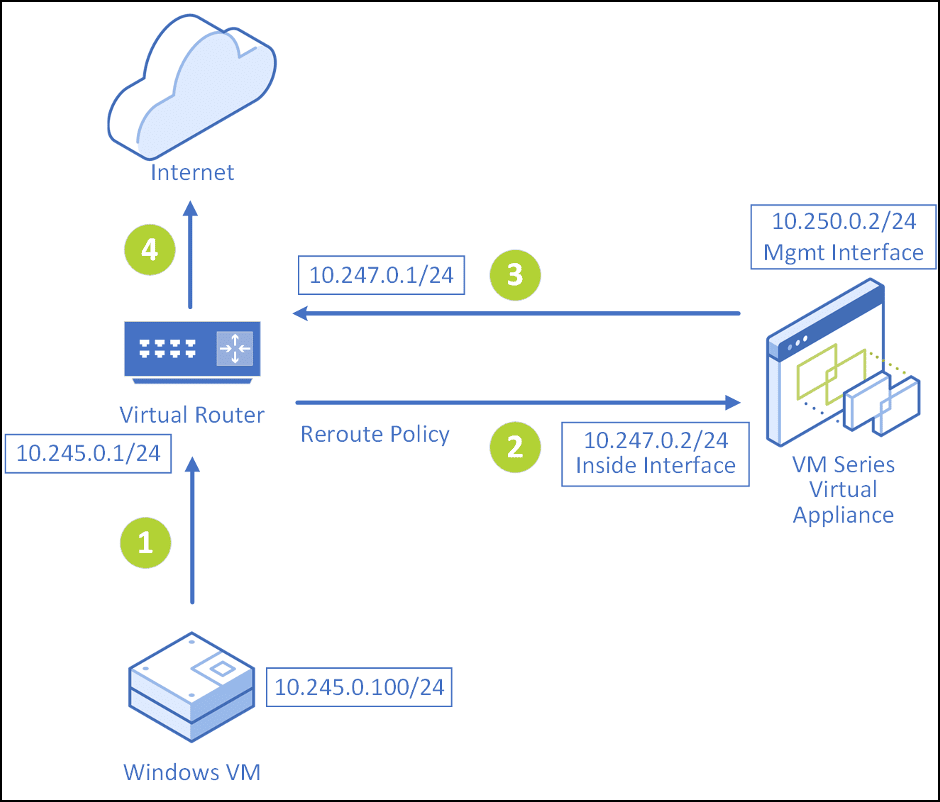
In the case of a single-legged VM-Series appliance, the desired traffic flow from the Windows VM to the internet would be as follows.
For outgoing traffic:
- Traffic from the VM (10.245.0.100/24) goes first to its default gateway, which is on the virtual router.
- Due to a reroute policy which needs to be added on Xi (shown in section - Configuring policies and rerouting Internet/VM traffic from VM-Series virtual appliance on Xi to on-prem firewall), the traffic is rerouted from the virtual router to the inside interface of the Palo Alto Networks appliance.
- A default route on VM-series virtual appliances is required to send 0.0.0.0/0 to its virtual gateway of its inside interface (i.e. 10.247.0.1/24).
- OPTIONAL: If you want your VM subnet to use the public IP assigned to the internal interface of the virtual appliance as the SNAT IP, create a NAT rule on VM-Series virtual appliance to source NAT VM subnet 10.245.0.100/24 to the internal interface IP of the virtual appliance 10.247.0.2; otherwise, it would use the SNAT IP of the production VPC where you have the virtual appliance deployed.
- Policies on Xi are required to permit the traffic from the Internet to 10.247.0.0/24 subnet in both the directions with a higher priority as compared to previous reroute policies, which will allow the traffic destined for the internet to go out from the virtual router to the internet. (shown in section - Configuring policies and rerouting Internet/VM traffic from VM-Series virtual appliance on Xi to on-prem firewall),
For return traffic:
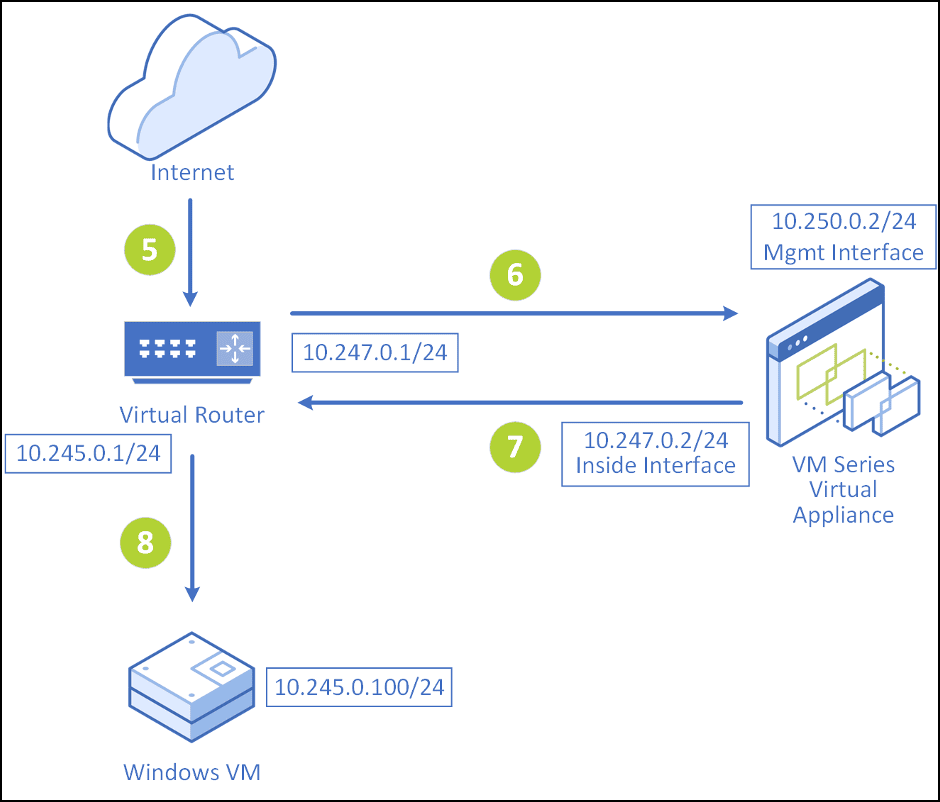
- The traffic comes from the internet and enters the virtual router. Due to the reroute policy configured on the Xi, the traffic is rerouted to the inside interface of the virtual appliance 10.247.0.2/24 (shown in section - Configuring policies and rerouting Internet/VM traffic from VM-Series virtual appliance on Xi to on-prem firewall).
- Since you already have a default route on the virtual appliance to send the traffic to its gateway 10.247.0.1/24, traffic is then forwarded to the virtual router.
- The default gateway present on the virtual router routes the traffic to 10.245.0.100/24.
If you have a floating IP (206.80.155.166) assigned to a VM (10.245.0.100/24), and you want to reroute all the traffic destined for the FIP coming from the internet, you would need to do the following:
- Have a reroute policy (i.e. traffic coming from the Internet to ANY/private subnet of the VM) to reroute the traffic to the inside interface (10.247.0.2) in a single-legged firewall.
- Have another reroute policy (i.e. traffic going to the Internet from ANY/private subnet of the VM) to reroute the traffic to the inside interface (10.247.0.2) in a single-legged firewall.
- Create policies on Xi to permit the traffic from Internet to 10.247.0.0/24 subnet in both the directions with a higher priority as compared to previous reroute policies, which will allow the traffic destined for the internet to go out from the virtual router to the internet.
- NOTE: For 1-3, refer to Configuring policies and rerouting Internet/VM traffic from VM-Series virtual appliance on Xi to on-prem firewall.
- Once the traffic is routed to the inside interface of the firewall, it is forwarded to the virtual router due to the route configured on the Palo Alto and down to the VM.
- Once the packet reaches the VM, the reply is sent to the virtual router, then rerouted to the inside interface of the firewall (due to the reroute policy), which sends it out to the internet.
Single-legged firewalls offer a simple design for this use case, but you would need to depend on IP policies instead of zones.
Issues Noticed with Two-Legged Design (Inside, Outside, and Management Interface)
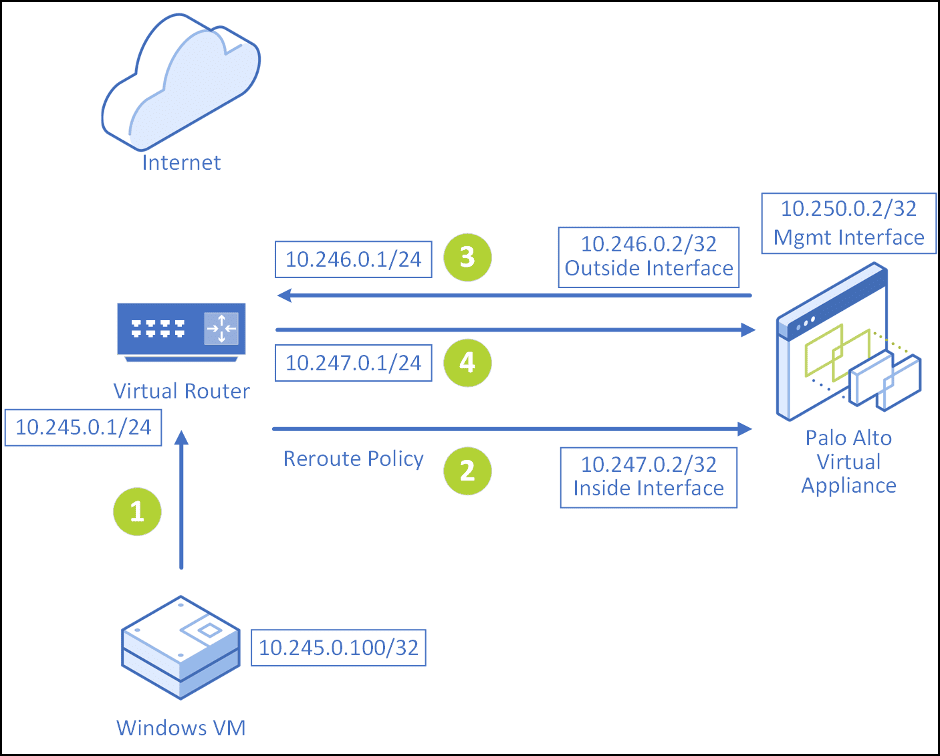
Nutanix has seen a looping issue on the Palo Alto Networks VM-Series device:
- Once traffic goes from Windows VM to its gateway on the virtual router and it gets rerouted to the inside interface of vPAN, you have a default route on the PAN to send it to 10.246.0.1.
- When the traffic reaches the virtual router, it will hit the reroute policy again and be sent back to the inside interface of the PAN. As a result, you see a continuous loop between the flows 3 and 4 as shown in the above diagram.
Nutanix does not have a way to avoid this from happening. Instead, Nutanix suggests the use of a single-legged design for virtual firewalls.
For deploying a Palo Alto Networks VM-Series Virtual Appliance on Xi.
 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.



