We are excited to announce a new feature that allows you to configure the User VM (UVM) as the default gateway for NC2 on AWS subnets. This eliminates the need for an EC2 instance to perform the gateway function, allowing you to use the existing bare-metal that you're already paying for with NC2. It also provides better security by forcing traffic to the gateway device without needing to change the local gateway on guest devices. This means there is no way to circumvent the firewall/gateway device.
The AWS Gateway implementation doesn't allow for just adding an NC2 VM as a gateway and carrying on. By default, the AWS gateway is .1 for each subnet, and routing changes require an AWS resource to configure routing. For example, using an EC2 instance, you would have to add AWS ENIs to your firewall/VPN to edit any traffic flows. You can see this in step 3 of this guide by Palo Alto.
With this new feature, a Nutanix Cluster can assign an AWS ENI to the NIC of an NC2 VM. In my example, I am going to be using Palo Alto to showcase this new feature.
NOTE: PC is not used in this workflow and this feature is for native networking only.
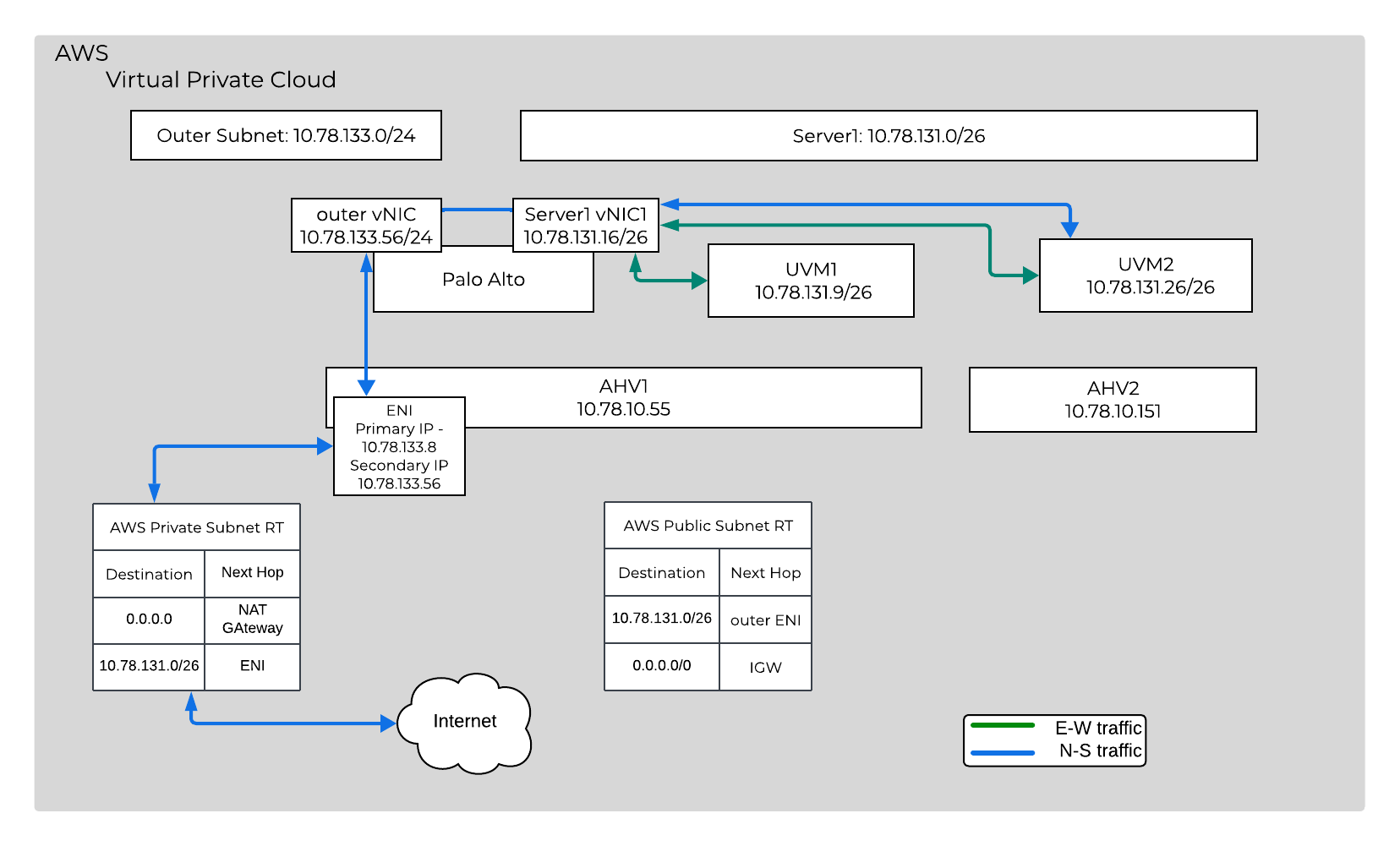
How It Works
The UVM gateway requires two or more interfaces:
-
Internal Interface (Inner Interface): This interface is configured with IP addresses for each inner subnet, enabling Layer 2 connectivity and routing traffic between different subnets. You can have multiple internal subnets. You would run the command below once for each inner interface you want to add.
API Configuration
To configure the UVM as the default gateway, use the following API endpoint:
-
URL:
http://localhost:9090/api/networks/<acropolis_subnet_uuid>/custom_gateway -
Method: POST
-
Request Body (JSON):
{
"gateway_internal_ip": "<IP address of the inner interface in gateway VM>",
"gateway_external_ip": "<IP address of the outer interface in gateway VM>",
"gateway_vm_uuid": "<UUID of the gateway VM>"
}
To Find the acropolis_subnet_uuid
acli
<acropolis> net.list
Network name Network UUID Type Identifier Virtual Switch Subnet
FirewallOutbound db3a2e0a-263c-4928-a4c1-567823a02380 kBridged 3 vs0 10.78.133.0/24
PC-Net 3e55d06f-b87a-4b55-bd9d-fddbd6632536 kBridged 1 vs0 10.78.129.0/27
p2p-external-subnet d1d3151d-9642-4cf7-8cb4-0c61f11c226f kBridged(External) 0 vs0 169.254.0.0/31
servers 8778a2fc-bab8-4cb6-9a0f-61ea6c890b07 kBridged 2 vs0 10.78.131.0/26To Find the UUID of the Gateway VM:
<acropolis> vm.list
VM name VM UUID
PAN-gateway 7f2450fc-7a52-4438-be45-a77ea43a73bd
- External Interface (Outer Interface): Once the above command is run, an AWS ENI is placed in both the private and public route tables. A route is added for each inner interface that is configured, pointing to the outer ENI. The UVM gateway outer interface will be consumed as a secondary IP on the ENI.
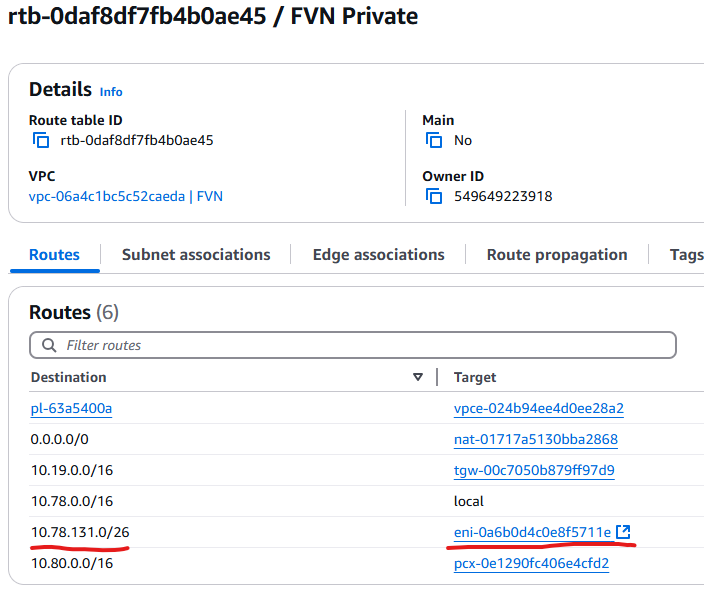
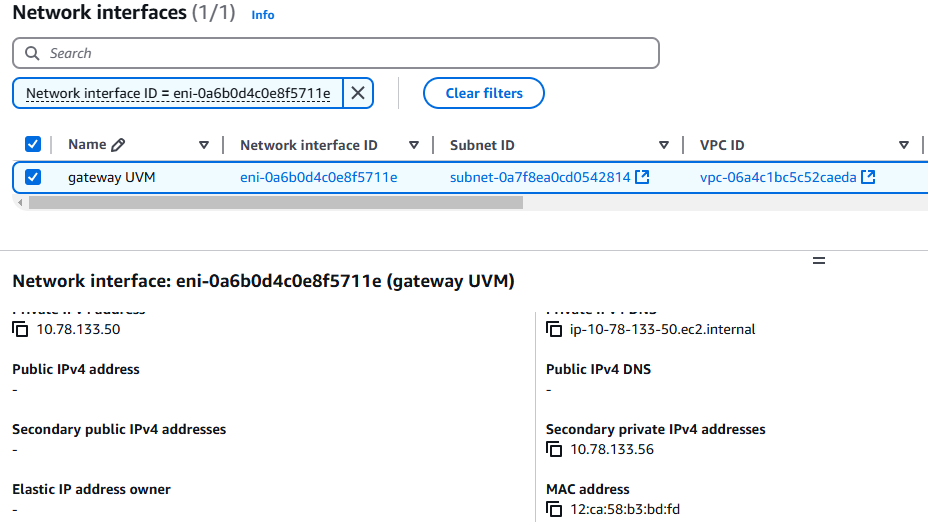
Below is the ENI that was added. In the image you can see the outer interface IP is added as a secondary IP.
The image below shows the interfaces from the Palo Alto VM. The managment interface was on ethernet1/0.
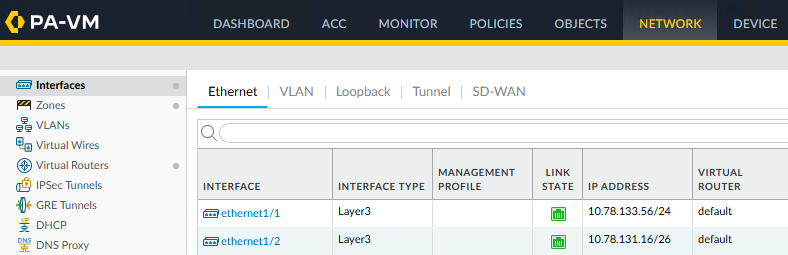
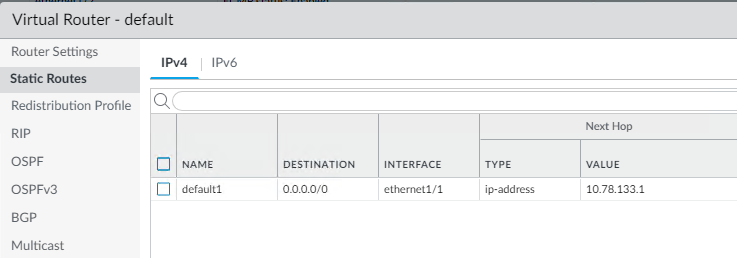
The default route for traffic leaving the Palo Alto will have it’s next hop set to the AWS defautl gateway for the outer interface subnet. The next hop is 10.78.133.1 since the AWS default gateway is always .1 for the given subnet CIDR.
After this your good to go! Typically you would have to change the default gateway for all of your guests vms. This would be done manually or maybe some scripting. Now imagine you have a DR event and you want to control the flow of traffic in the new environment. Not only you don't have to go into every machine and change it, when you failback there is no extra work to do! Not to mention all of the security benefits of ensuring that nothing can be tampered with in the guest to change the flow of traffic. This is possible because after the command is ran, OVS flows will be installed on the AHV hosts to force traffic to the Palo Alto.
Prerequisites
Before configuring UVM as the default gateway, ensure the following:
-
The UVM must have an internal interface on each non-default subnet it will serve as the gateway for.
-
The external interface must be in a subnet that uses the AWS gateway (not a UVM gateway).
-
Management subnets (e.g., AHV/CVM, Prism Central) should always use the AWS default gateway for routing.
Conclusion
This new feature provides greater control and flexibility over your network traffic within NC2 on AWS and limit the cost of needed EC2 instances.
We encourage you to explore this new feature and share your feedback with us. If you have any questions or need assistance, please reach out to our support team.
Thank you for choosing Nutanix!

