The Flow Gateway VM (FGW) for Nutanix Cloud Clusters In Azure(NC2) is the Lynch pin to having a your own Supercloud. The FGW is responsible for all VM traffic going north and south from the Nutanix cluster in Azure. This virtual machine allows outside communication from both cloud and on-premises services to the workloads running on the Azure NC2 Cluster.
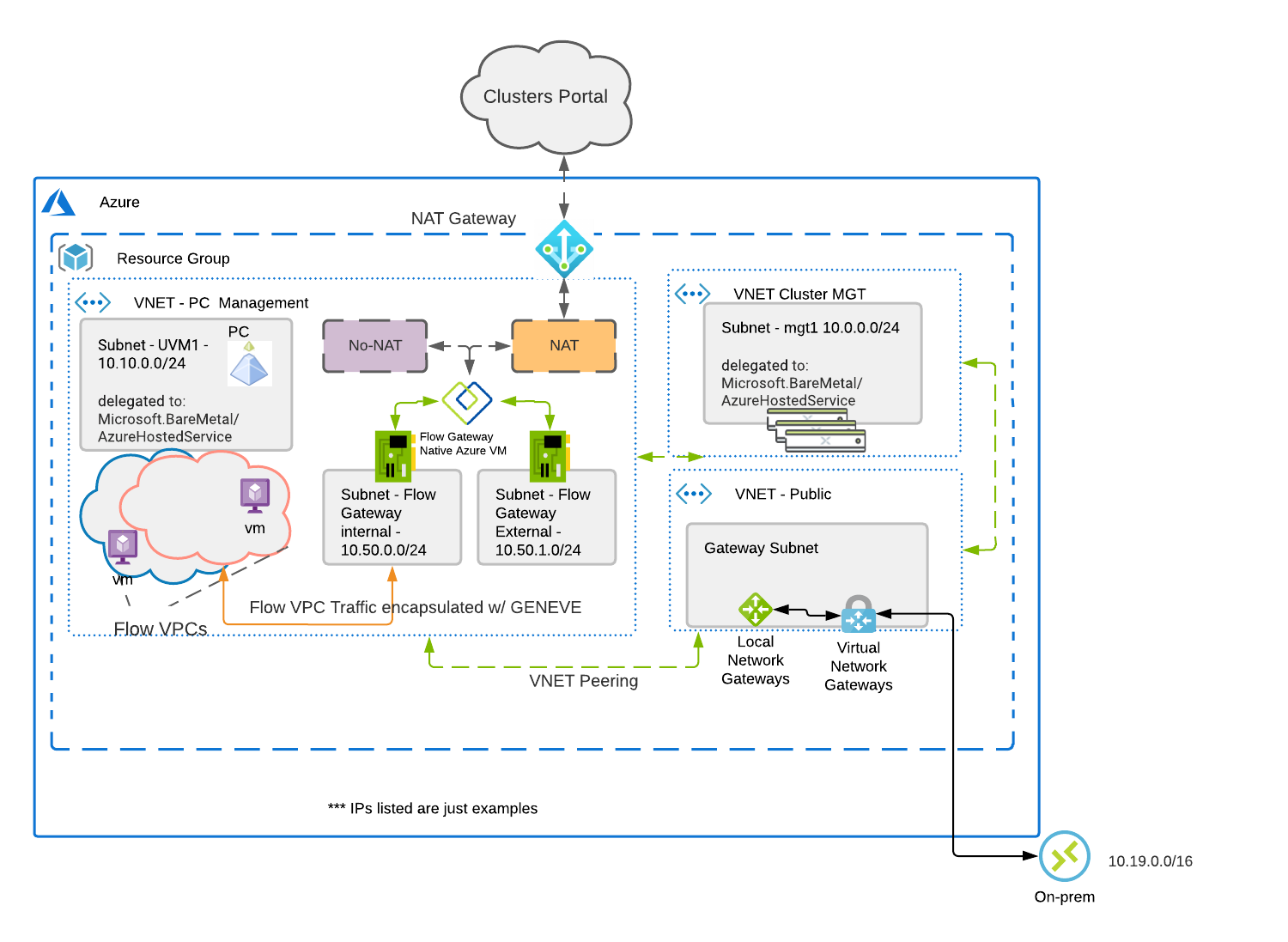
Once Prism Central is automatically deployed from the cluster creation process, the FGW deploys into the same VNET that Prism Central is using. The FGW is a native Azure VM. The VM has two network interface cards(NICs) attached to it, one for internal traffic and one for external traffic. The external NIC where the floating IP's are configured for workloads that may need away outside clients connecting into running workloads on the cluster. The default installation will configure 50 floating IP's on the external NIC. These floating IP's can be assigned in Prism Central in the VM menu or in the VPC menu.
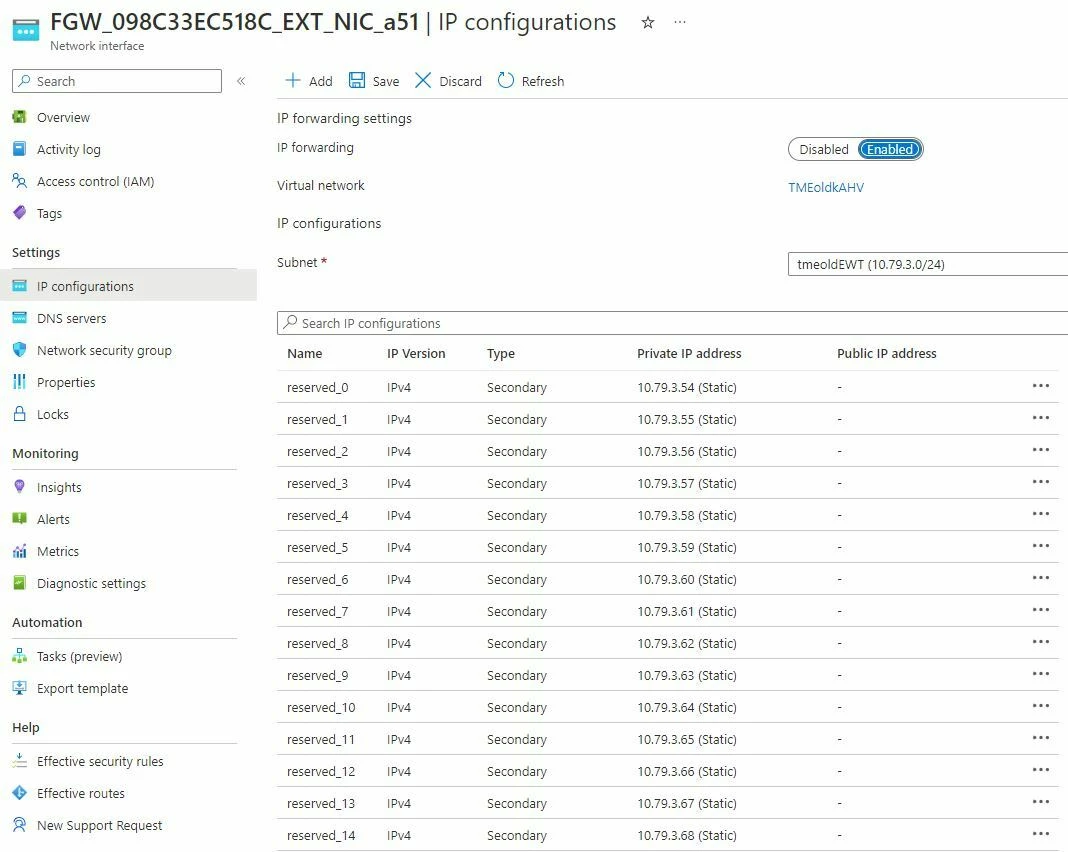
When sizing the subnets for the FGW I would use the following miniums.
The internal subnet - /28
The external subnet - /25
For production deplpyments I would double the size of the above subnets for future growth.
Traffic that goes directly to the hypervisor, the storage controllers and Prism Central are not in the path of the FGW. This is important because replication traffic can represent most of the bandwidth coming from on-prem when you go to migrate/failover workloads to Azure.
The current sizes for the FGW are:
Small (Standard_D4_v4, 4 vCPUs, 16GiB RAM) - Expected network bandwidth (Mbps) 10000 Mbps
Large (Standard_D32_v4, 32 vCPUs, 128GiB RAM) - Expected network bandwidth (Mbps) 16000 Mbps
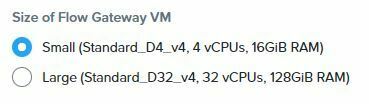
With the large price difference between the two types it's best to start small and then you can always change the VM type later. If you do need to change the VM type, your network security group settings will be preserved on the VM.
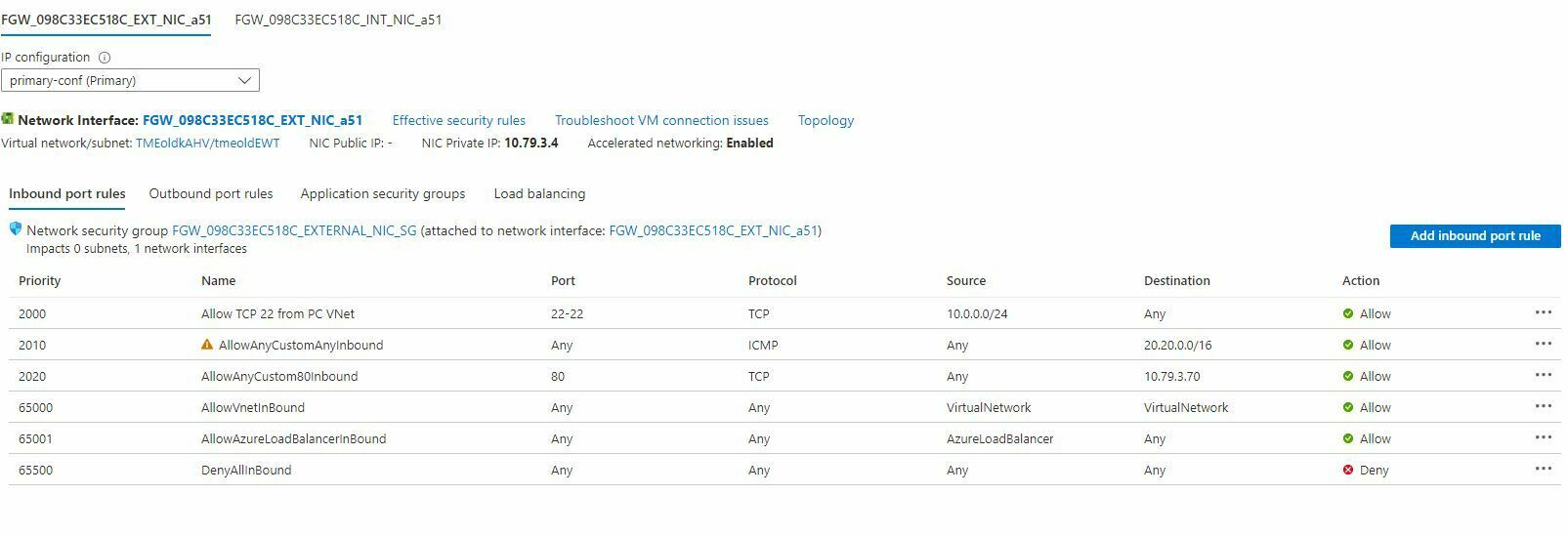
Both the internal and external NICS have a network security group (NSG) Attached to them. In most cases you will have to adjust the external NSG to allow traffic into the cluster.
As of today the FGW is a single VM. If the FGW is stopped or deleted , The NC2 portal will see it as HA event where FGW is unreachable and then portal will create a new FGW in place of existing if it exists or delete FGW which is powered off. When I was testing upgrades of the FGW it took four minutes to perform an upgrade from the NC 2 portal. It follows a similar process of removing and replacing the VM with a new one.
Hopefully that covers everything you need to know about the Flow Gateway VM in Azure. If you do have a question, ask away!
NC2 on Azure Networking Training →

