It’s been one year since we formally launched Nutanix Flow at .NEXT 2019 in NOLA. The past year has been an incredible one for us in many ways - as customers started using Flow we learned a lot about their specific challenges, microsegmentation, and the state of Software Defined Networking (SDN). Every customer we spoke to about Flow loves the simplicity of our microsegmentation offering - enabled and configured with just a few clicks, with nothing to install and backed by APIs and built-in automation. During these discussions, we also uncovered the challenges that new and current technologies have created. Below, we share those findings, lessons learned and the future of Flow. First, let’s take a quick look at how our customers are using Flow:
Network Segmentation: Using Flow to segment virtual networks with software instead of physical devices or VLANs, reducing network complexity and embracing “software-defined”. Flow allows customers to avoid physical network silos and complexity. The Flow visual policy model allows easy changes to configurations or migration and promotion of workloads between security zones. Examples include: separating development from test virtual machines (VMs), creating a DMZ, segmenting based on workloads such as virtual desktops from HR applications.
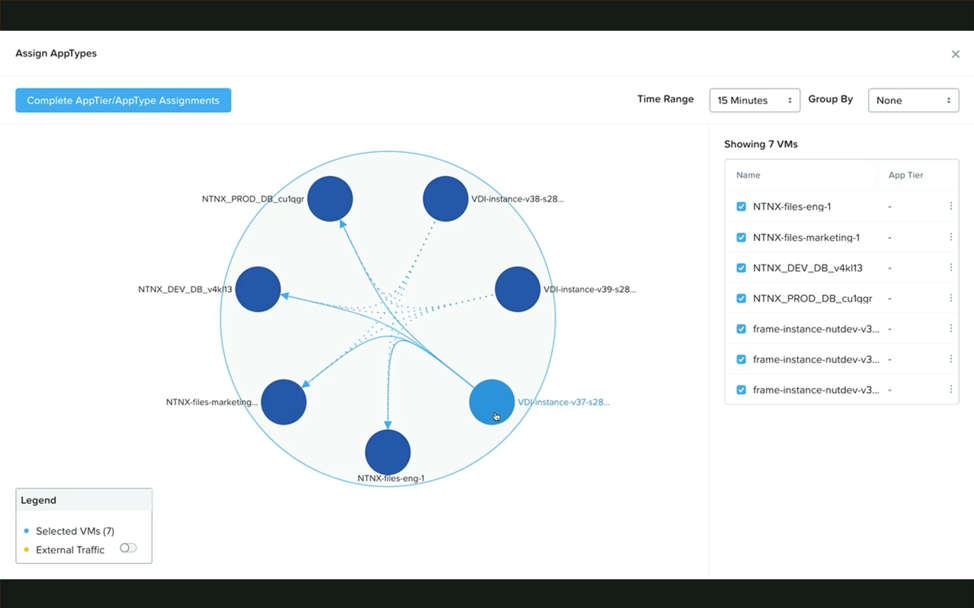
Application Segmentation: Using Flow to enhance security by limiting application communications to only what’s necessary. This limits malware’s ability to spread between applications or application tiers. For example, web servers should only talk to application logic VMs and application logic VMs should only talk to database VMs. Further, web servers should not be able to talk with each other.
End User Computing / Virtual Desktop Security (Citrix and Frame): Using Flow to secure desktops based on user groups or categories with a simple security policy can prevent malware spread and other threats.
Regulatory Compliance: Using Flow to address regulatory requirements for segmentation without creating dedicated islands of infrastructure. For example, meeting Payment Card Industry(PCI) and HIPAA requirements on the same physical infrastructure that runs non-regulated workloads.
The Current State and the Need for Frictionless
Let’s discuss how the limitations of existing technology are creating friction. New technologies like microsegmentation and SDN have brought agility and speed, but they have added complexity and created their own new silos.The Traditional Approach
In the traditional application lifecycle, the application developer develops apps, the VI admin deploys and manages the app infrastructure, and the network admin configures networks (whether they’re SDN or physical) and the security admin configures security policies (as needed). This creates several layers of silos across the organization. (This is still a prevalent mode of operation in many large and small enterprises). Maneuvering through these silos slows down application deployment and often leaves East-West application (around 80% datacenter communication) traffic security to a best effort, or none at all.
Microsegmentation
Microsegmentation eases some of the friction of the traditional approach by integrating security functionality in the hypervisor and virtual network. The hypervisor already has the context of the virtual machines and thus is the perfect location to insert network controls at a very granular VM level. Microsegmentation has been around for quite some time, yet it has not seen wide adoption due to added complexity in the planning, configuring, and operating.
Networking
Networking is another area that has not been completely addressed, even with SDN. SDN created agility with API based network provisioning and management tied to application lifecycle management. However, most enterprises are still not able to achieve this end-to-end automation. This is largely due to organizational issues of the networking team doing network automation and the virtualization team doing VM automation. We have spoken to several large enterprises who still struggle with the pain of running separate networking and virtualization silos, while the smaller and mid-market companies struggle with the cost, complexity, and skills required to manage the SDN infrastructure.
Flow = Frictionless Networking, Microsegmentation
Flow was built from day one to address the challenges of the traditional approach and unfulfilled promises of more novel offerings. We have been laser-focused on design simplicity. Your microsegmentation journey should NOT start with redesigning networks (underlay or overlays). You don’t have to be a security ninja to write policy and automate with Flow. Constructs like categories and pre-defined policies which get applied or removed as VMs are added or deleted throughout the application lifecycle make security simple and app focused. We have invested in removing the separation between the networking, security and virtualization teams. In the modern application lifecycle with Nutanix Flow, VMs are created with the correct categories, placed into easy to design visual policies, and their network is protected by default on first-boot.
In the area of network automation - Flow and AHV API-based extensions allow the virtualization layer to share that invaluable context and awareness with the network — in this case, the networking vendors, such as Arista, BigSwitch, Juniper, Mellanox, and more. Context allows the network fabric to automatically create, trunk, and prune VLANs based on real-time VM events. The networking team can select the best-of-breed solution and know that their selection will work great with Nutanix and our automated virtual environment.
Not only have physical networking vendors embraced the Nutanix vision, but major firewall vendors have joined as well to bring enhanced inspection that compliments Flow microsegmentation. Firewall VMs from CheckPoint, Juniper, Palo Alto Networks, and more are certified to run on Nutanix AHV with Flow traffic redirection for additional traffic inspection and threat detection.
Future of Frictionless Microsegmentation with Flow
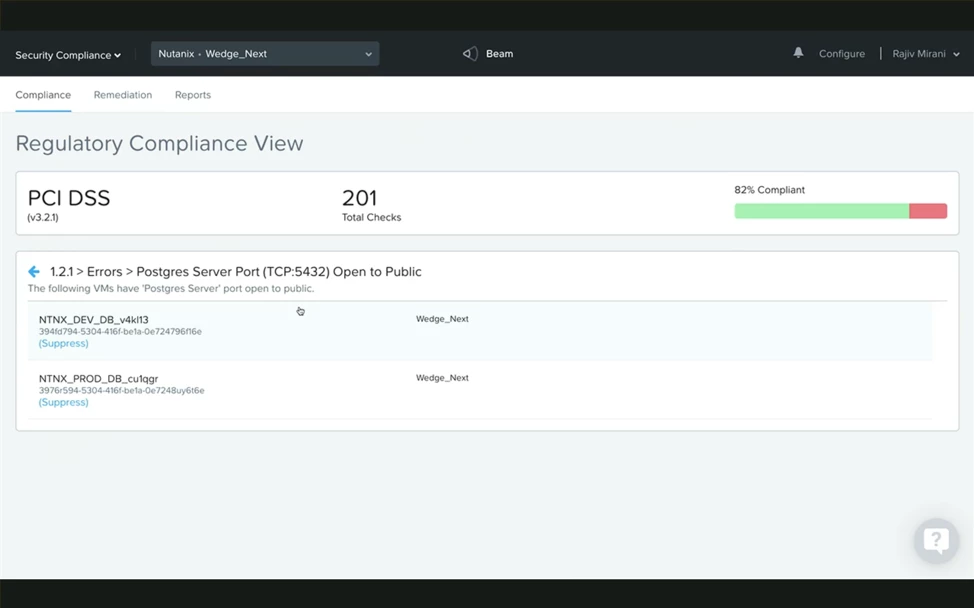
Looking forward, we are investing heavily in simplifying microsegmentation further with end to end visualization, automatic policy generation, and integrating Active Directory identity into security policies. Many microsegmentation deployments struggle because of the lack of skills in policy authoring, but with built in visualization and automatic policy generation, Nutanix admins can achieve their security goals without the friction and challenges that microsegmentation often brings.Many small customers also struggle with the complexity of achieving compliance and have anxiety over handling compliance audits. In the future we’re planning to integrate our Beam security compliance tools with Flow to ease the work, planning, and stress involved in achieving compliance such as PCI-DSS with Flow. Together, Beam and Flow can produce regular reports on workload compliance, provide easy auditing capability, and respond to violations with remediation suggestions.
Imagine your modern datacenter. You can automate security with application deployments on top of any SDN based physical fabric. Automate policy with app deployment. Define policy with aided visualization. Achieve compliance without physical silos and handle audits without months of evidence collection. All with one-click built-in integration. That’s frictionless! That’s the journey we have embarked on with Flow.
We are not stopping there. With Flow we are on a mission to secure every application that runs on Nutanix AHV, including our own applications and services. Whether you are securing a 3-Tier App, Microsoft, Oracle, Splunk, Nutanix Era (Databases), Nutanix Files, or Nutanix Frame DaaS workloads, we have you covered with Flow and frictionless security.
Want to learn more? You can get a quick demo (scroll to the very bottom) or read up on Flow here. If you missed us at .NEXT, check out Sunil’s Day 1 Keynote where we show automation for the security of VDI and database workloads with Beam, Epoc, and Flow. Join us and see more in person at a .NEXT on Tour or at .NEXT Europe in Copenhagen on October 8-10.
Disclaimer: This blog may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site.
Forward Looking Disclaimer
This blog post includes forward-looking statements concerning our plans and expectations relating to new product features and technology that are under development, the capabilities of such product features and technology and our plans to release product features and technology in future releases. These forward-looking statements are not historical facts, and instead are based on our current expectations, estimates, opinions and beliefs. The accuracy of such forward-looking statements depends upon future events, and involves risks, uncertainties and other factors beyond our control that may cause these statements to be inaccurate and cause our actual results, performance or achievements to differ materially and adversely from those anticipated or implied by such statements, including, among others: the introduction, or acceleration of adoption of, competing solutions, including public cloud infrastructure; a shift in industry or competitive dynamics or customer demand; and other risks detailed in our quarterly report on Form 10-Q filed with the Securities and Exchange Commission. These forward-looking statements speak only as of the date of this press release and, except as required by law, we assume no obligation to update forward-looking statements to reflect actual results or subsequent events or circumstances.
© 2019 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and the other Nutanix products and features mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s), and Nutanix may not be associated with, or sponsored or endorsed by such holder(s). This document is provided for informational purposes only and is presented ‘as is’ with no warranties of any kind, whether implied, statutory or otherwise