HI
Are your user vms on a different subnet than the CVM? They shouldn’t use the baremetal subnet. I assume AWS native networking so you need to edit the UVM security group that was deployed with the cluster to allow ssh. You can send an email to dwayneATnutanix.com and I can setup a zoom.
Thanks for your response. I have sent an email to dwayne@nutanix.com. Please let me know when you can setup the meeting.
Hi Sharti,
Thanks for the screenshot. I’m not sure if you have resolved the issue but here’s a suggestion: You’ve deployed Nutanix Cloud Clusters (NC2) on AWS, and Prism shows the cluster is healthy. However:
Current Issue:
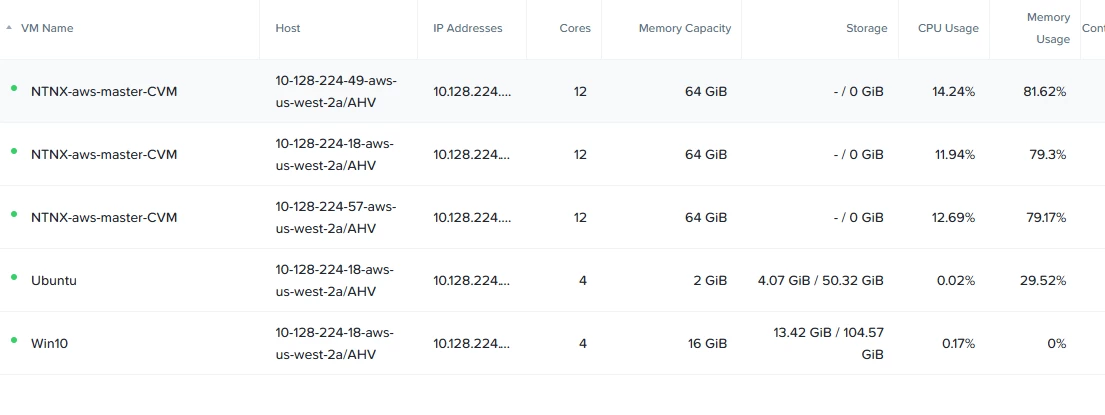
- VMs (Ubuntu and Win10) cannot access the internet (no updates/downloads).
- SSH access to VMs fails.
- CVMs are healthy, but guest VMs appear isolated.
Confirmed from Screenshot:
- CVMs are distributed across hosts, healthy.
- Ubuntu and Win10 VMs show low CPU usage, implying they are running but idle/network-bound.
- No external network activity is visible.
- This is a common Day 2 networking gap with NC2 on AWS.
Root Cause (Most Probable):
NC2 VMs do not get internet access by default unless:
- A NAT gateway or Internet Gateway (IGW) is attached to the subnet.
- Security Groups (SGs) allow:
- Outbound egress (e.g., 0.0.0.0/0 on TCP 80/443).
- Inbound SSH/RDP from your IP.
- AHV virtual NICs (vNICs) are correctly mapped to VPC subnet bridges.
- The default gateway and DNS inside the VM are set to AWS's VPC IPs.
What You Need to Check and Fix
1. Is There a NAT Gateway or IGW?
In AWS VPC:
- Go to your VPC > Route Table.
- Verify that the subnet where your guest VMs are running has:
- Destination: 0.0.0.0/0 → Target: nat-xxxxxxxx or igw-xxxxxxxx
If not:
- Add a NAT Gateway for private subnets or an IGW for public subnets.
- Ensure the route is added to the route table.
2. Security Group Rules
For the ENIs (Elastic Network Interfaces) assigned to your AHV/VM NICs:
- Egress (Outbound)
- Allow all traffic: 0.0.0.0/0, TCP, UDP
- Ingress (Inbound)
- Allow SSH (TCP 22) and/or RDP (TCP 3389) from your public IP
Also check the AWS Network ACLs ensure they are not denying egress.
3. Prism Virtual Switch Mapping
In Prism (AHV networking view):
- Ensure that the VM NICs are attached to a bridge that maps to the AWS subnet (usually br0 or custom bridge).
- Verify that the uplink is active and bonded to the proper VPC ENI.
Use this on CVM to check:
manage_ovs show_bridges
4. Guest VM Default Gateway and DNS
Inside the VM:
- Run ip a and ip r (or route -n) to check default route.
- Run
cat /etc/resolv.conf (Linux) or ipconfig /all (Windows) to verify DNS.
Make sure the default gateway is the VPC router IP (usually something like 10.128.0.1) and that DNS is either:
- AWS default DNS
- Or external (e.g., 8.8.8.8), if explicitly routed
Optional Test: Ping from CVM
From a Nutanix CVM:
ping google.com
curl -v https://mirror.centos.org/
If the CVM can reach the internet, but the guest VM cannot, it confirms the AHV-to-guest network bridge mapping is the problem.
Conclusion and Next Steps
- Validate your AWS networking (NAT/IGW, route table).
- Check AHV vSwitch mappings in Prism.
- Fix guest VM security group and network interface config.
- Test from inside VM and/or from CVM.