Hello Team,
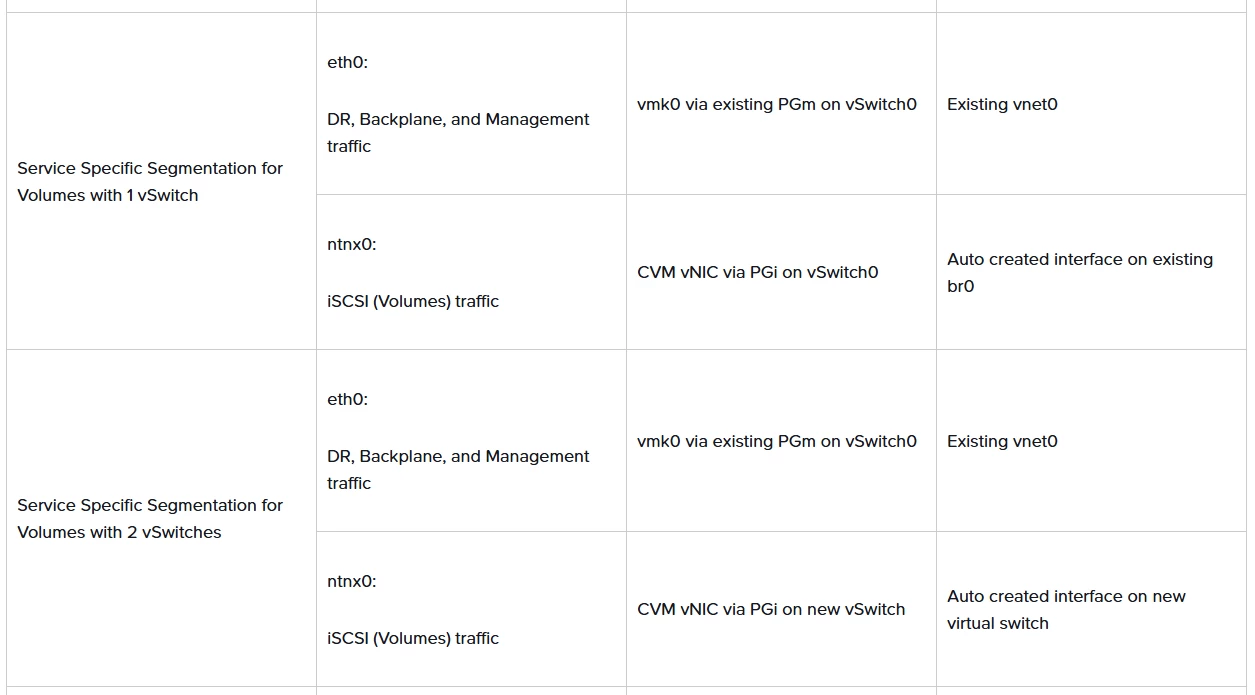
One of our customer have a requirement to use a different subnet for Nutanix Volume iSCSI IP address than the CVM IP subnet range.
This is because he wants the iSCSI volume traffic not to flow via his firewall. So he intent to use IP subnet for iSCSI Volume same as the VM (iSCSI Initiator) range.
Going by the documentation https://portal.nutanix.com/page/documents/details?targetId=Volumes-Guide:vol-volumes-external-ip-address-c.html, it states:
“This IP address should be in the same subnet as the cluster Controller VM IP eth0 network interface addresses”
Is this a mandatory requirement?
Thank you in advance!