Our patented browser-based, SSO solution for Windows Active Directory domain-joined VMs
Frame® customers now have early access to the new Frame SSO feature, which provides Windows® Active Directory (AD) SSO into virtual apps and desktops — all from your Frame Dashboard (Settings > Domain Settings > Frame SSO) on a per Frame Account basis.
This blog guides you through a deep-dive on this industry leading feature, how it works and how it compares to other solutions from other DaaS vendors, and why we believe Frame SSO is a game-changer.
Background
The desktop-as-a-service (DaaS) industry continues to face a long-standing challenge in providing AD SSO into Windows domain-joined virtual desktops. Users are typically required to log in at least twice — once to their DaaS platform and a second time to AD if the VM hosting their session is domain-joined.
Further complicating this issue, different sets of credentials — usually a SAML 2.0-based identity provider like ADFS, AzureAD, Google, or Okta — are often required to initially access DaaS and AD credentials before logging on to the Windows VM.
The root of the issue is that with SAML, AD does not have access to the user’s password and there are only two logon methods:
- Explicit credentials (username and password)
- Smart card logon
Smart card logon leverages digital certificates to provide authentication. The certificate is issued by a trusted certificate authority (CA). When a user presents a smart card upon logon, the AD domain controller retrieves the user’s certificate from AD and checks that it is valid and issued by a trusted CA. If it is valid and the CA is trusted, the user is granted access to the domain.
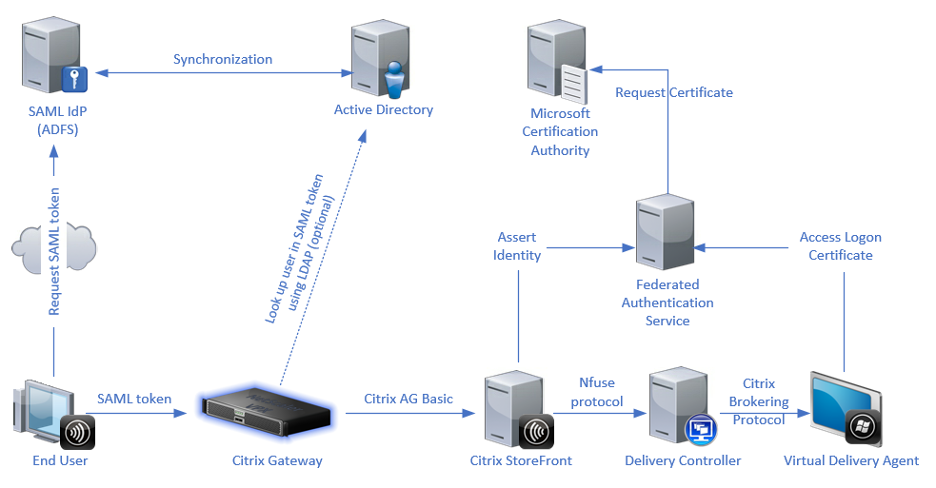
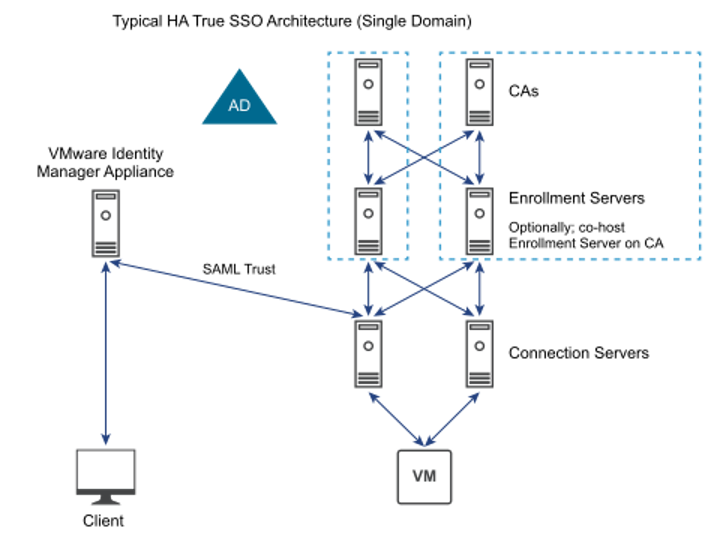
Nearly all DaaS vendors that offer an AD SSO solution today, including Citrix Federated Authentication Services and VMware Horizon True SSO, leverage smart card logon using virtual smart cards.
The problem with this approach is that it adds complexity and requires an assortment of components to manually deploy, manage and maintain. Customers also need to create shadow user accounts for every DaaS user within their AD domain with user principal names (UPNs) that match the user's SAML attribute such as an email address.
The benefit of this approach is that, once it is properly configured, it is completely seamless to end users.
Citrix Federated Authentication Services (FAS) Architecture. Source, June 16, 2021
VMware Horizon True SSO Architecture. Source, May 16, 2022
A better, simpler and more modern approach
Nutanix Frame has always incorporated a browser-first core design principle. This gives customers and users seamless, cross-platform access. By leveraging the browser as the primary client, users can access their apps and desktops from any device with a modern web browser — just like they already do everyday with work and personal web apps.
For IT, this approach enables the majority of our customers to eliminate client-side software installations and configurations, which can be time-consuming, problematic or impossible with personal devices. It also allows for easy scalability and a more agile deployment model to quickly onboard new users by expanding into new or existing use cases.
Frame SSO architecture and workflow
Instead of smart card logon, Frame SSO uses explicit credentials supplied by the user upon initial registration or reregistration. Once registered, credentials are automatically encrypted and stored on the user’s local browser or Frame App.
The next time the user logs into their Frame account from the same device/browser or Frame App, the credentials are automatically retrieved from storage and passed to the Frame workload VM hosting the session.
This design requires no additional components or administrative configurations outside of enabling the Frame SSO toggle within the dashboard of the Frame accounts for which you would like to leverage the feature. Administrators don’t have to worry about additional setup when a new user is onboarded or when an existing user needs to be off-boarded from Frame.

This patented approach to Windows AD SSO is unique to Frame.
Now let’s take a look at the two workflows for Frame SSO in detail:
No stored credentials workflow
This is the workflow for the following scenarios:
- Initial registration of user AD credentials with Frame SSO for a particular Frame account from a specific device/browser.
- Reregistration of AD credentials if the stored credentials are either expired or invalid.
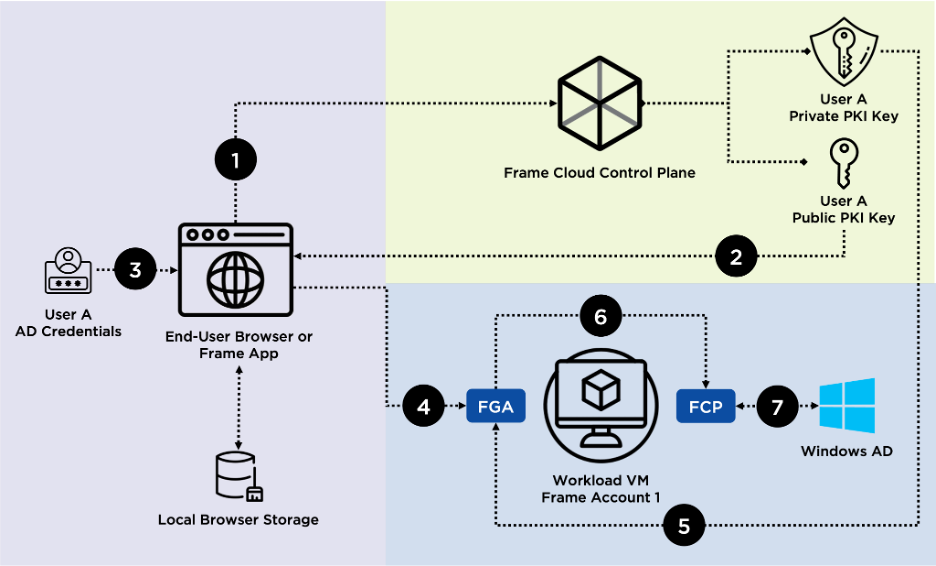
1. User A starts a session to Frame Account 1 via their browser. Frame detects there are no encrypted AD credentials stored for User A for Frame Account 1 within their device/browser.
2. The public PKI key for User A is obtained from the Frame control plane and will be used to encrypt the User A’s AD credentials for use with Frame SSO.
3. Frame prompts User A to enter their AD credentials with Frame SSO and uses the public PKI key to encrypt the supplied AD credentials and stores them as ciphertext within the local browser storage on User A’s device.
4. The encrypted credentials are then sent to the Frame Guest Agent (FGA) running on the workload VM for Frame Account 1.
5. FGA requests and is supplied with the corresponding private PKI key for User A from the Frame control plane.
6. FGA uses the private PKI key to decrypt User A’s credentials in memory and sends the credentials to the Frame Credential Provider (FCP) on the workload VM for Frame Account 1.
7. FCP then utilizes the decrypted credentials to initiate an interactive logon to AD. If there are any errors with the supplied credentials (invalid, expired, etc.), FCP notifies Frame Terminal, which deletes User A’s stored credentials for Account 1 and returns to Step 1.
Stored credentials workflow
This is the workflow when Frame detects there are stored AD credentials available on the user’s device/browser for the particular Frame Account they are attempting to start a session to:
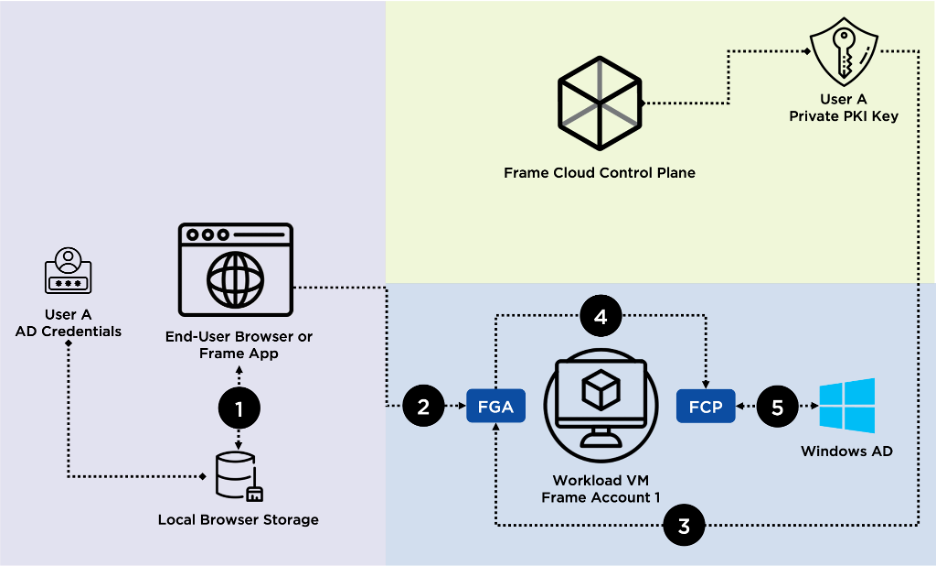
1. User A starts a session to Frame Account 1 via their browser. Frame detects there are encrypted AD credentials stored for User A for Frame Account 1 within their device/browser.
2. The encrypted credentials are retrieved from User A’s local browser storage and sent to the Frame Guest Agent (FGA) running on the workload VM for Frame Account 1.
3. FGA requests and is supplied with the corresponding private PKI key for User A from the Frame control plane.
4. FGA uses the unique private PKI key to decrypt User A’s credentials in memory and sends the credentials to the Frame Credential Provider (FCP) on the workload VM for Frame Account 1.
5. FCP then utilizes the decrypted credentials to initiate an interactive logon to AD. If there are any errors with the supplied credentials (invalid, expired, etc.), FCP notifies Frame Terminal, which deletes User A’s stored credentials for Account 1 and initiates the No Stored Credentials Workflow.
Advantages and Caveats
Advantages
The advantages of Frame SSO are pretty clear:
1. Frame SSO requires no additional components and complexities required such as CAs, SSO service servers (and load-balancing for those servers for high-availability), user shadow accounts, etc.
2. Frame SSO is secure by design. Stored credentials are encrypted with AES-256 and only stored on the user’s local device. The PKI key pair for encrypting and decrypting the credentials are only stored in Frame’s control plane.
3. Admins can enable the feature on any Frame account (that’s already AD domain-joined) with a single click.
4. No additional setup or clean-up required when new users are onboarded or when existing users need to be off-boarded from Frame.
5. User registration of their AD credentials with Frame SSO is simple and intuitive.
Caveats
There are, however, some caveats that customers should be aware of before enabling Frame SSO:
1. Registered credentials are stored on a per-Frame account, per device, per browser or Frame App basis. This means that if a user accesses a single Frame account from two separate devices, they must register their credentials twice — once on each device. User access to multiple Frame accounts from the same device requires credential registration for each Frame account that has Frame SSO enabled.
Note: For shared desktop/device use cases, Frame SSO does support storing multiple encrypted AD credentials on the same device for different users. However, Frame SSO does not support the use case where a user needs to use multiple AD credentials when accessing the same Frame account.
2. Frame SSO is not aware if AD credentials are expired or invalid until the credentials are passed to the domain controller. This means that Frame is unable to warn users if their AD credentials are expired or invalid until they try to start a session. If the credentials are expired or invalid, users must work with their help desk or admin to address their credential issue outside of Frame and then register their credentials again with Frame SSO.
3. Admins are unable to delete/reset locally stored credentials for users on their behalf. Users can delete them by following the instructions here.
More enhancements and a test drive
We hope you are as excited about the release of Frame SSO to early access as we are. We see Frame SSO as another key differentiator for Frame in the market, as well as a solution that will help organizations accelerate their adoption of DaaS by streamlining the end-user experience without adding additional complexity or overheads.
While we already have a number of enhancements planned for the Frame SSO general availability release later this year, we encourage customers and prospects to test Frame SSO now and let us know what you think.
You can reach out to us at frame-sales@nutanix.com or on social media (LinkedIn and Twitter).
To learn more about the feature, check out our Frame SSO technical documentation here.
About Frame
Apps and desktops, simplified. That’s what DaaS should be and that’s what Frame is.
Whether you are a large enterprise, SMB, K-12/higher education institution or a service provider, we look forward to helping you and your organization be better prepared for tomorrow’s challenges.
If you’re interested in learning more about Frame, check out this four-minute demo video that highlights our key user interface and indispensable administrative features.
Want to try Frame for yourself? You have a couple of options:
- Take Frame on a free 12-hour test drive in AWS.
- Start a free 30-day trial in your infrastructure of choice.