AOS 6.7 has added more options for securing your cluster in AWS. We will take a look at the existing options and dive into the new feaure in AOS 6.7.
You can use AWS security groups and network access control lists to secure your cluster relative to other AWS or on-premises resources. Nutanix automatically creates three security groups to limit traffic to the cluster:
- Internal management: Allows all internal traffic between all CVMs and all AHV hosts (EC2 bare-metal hosts). Don’t edit this group without approval from Nutanix Support.
- User management: Allows users to access Prism Element and some other services running on the CVM.
- UVM: Allows UVMs to talk to each other. By default, all UVMs on all subnets can talk to each other, but you can edit the policy to lock down more traffic. You could alternatively use Flow Network Security to prevent east-west traffic.
With AWS security groups, you can limit access to the AWS CVMs, AHV host, and UVMs only from your on-premises management network and CVMs. You can control replication from on-premises to AWS down to the port level, and you can easily migrate workloads because replication software is embedded in the CVMs on both ends.
AOS 6.7 adds support for custom AWS Security Groups. Prior to this update, two main security groups provided native protection. The new enhancement provides additional flexibility so AWS security groups can apply to the Virtual Private Cloud (VPC) domain and at the cluster and subnet levels.
Custom AWS Security Groups are applied when the ENI is attached to the bare-metal host. You can use and reuse precreated Security Groups across different clusters without additional scripting to maintain and support the prior custom Security Groups.
You can use the tags in the following list with any AWS Security Group, including custom Security Groups. The Cloud Network Service (CNS) uses these tags to evaluate which Security Groups to attach to the network interfaces. The CNS is a distributed service that runs in the CVM and provides cloud-specific back-end support for subnet management, IP address event handling, and security group management. The following list is arranged in dependency order.
- Scope: VPC
- Key: tag:nutanix:clusters:external, Value: <none>, (leave this tag blank)
- You can use this tag to protect multiple clusters in the same VPC.
- Scope: VPC or cluster
- Key: tag:nutanix:clusters:external:cluster-uuid, Value: <cluster-uuid>
- This tag protects all the UVMs and interfaces that the CVM and AHV use.
- Scope: VPC, cluster, network, or subnet
- Key: tag:nutanix:clusters:external:networks, Value: <cidr1, cidr2, cidr3>
- This tag only protects the subnets you provide.
If you want to apply a tag based on the subnet or CIDR, you need to set both external and cluster-uuid for the network or subnet tag to be applied.
The following subsections provide configuration examples.
Default Security Groups
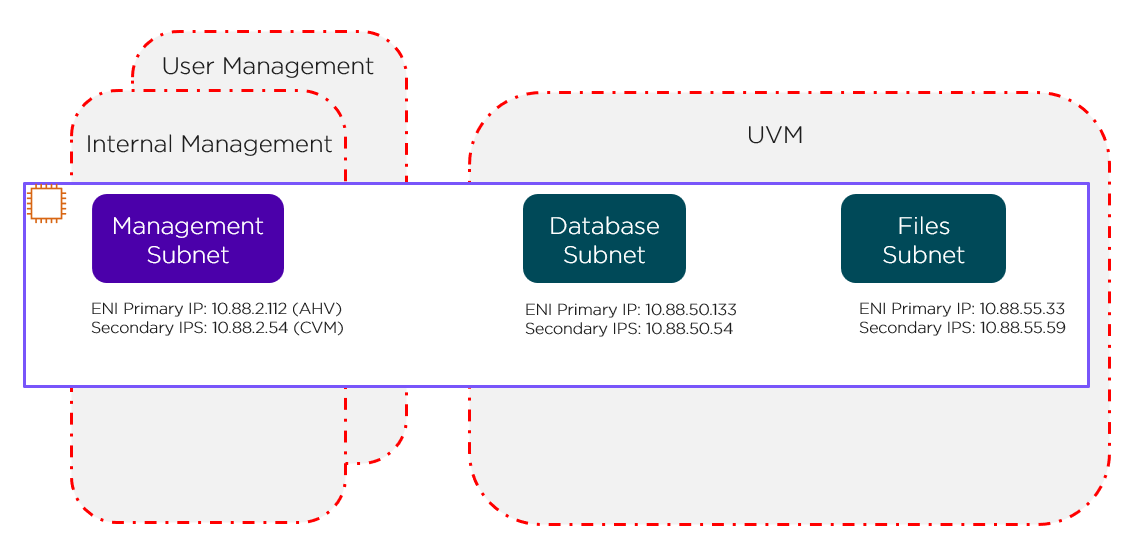
The red lines in the preceding figure represent the standard AWS Security Groups that deploy with the cluster.
- Internal management Security Group: Allows all internal traffic between all CVMs and AHV hosts (EC2 bare-metal hosts). Don’t edit this group without approval from Nutanix Support.
- User management Security Group: Allows users to access Prism Element and other services running on the CVM.
- UVM Security Group: Allows UVMs to talk to each other. By default, all UVMs on all subnets can talk to each other. This Security Group doesn’t offer subnet granularity.
VPC Level
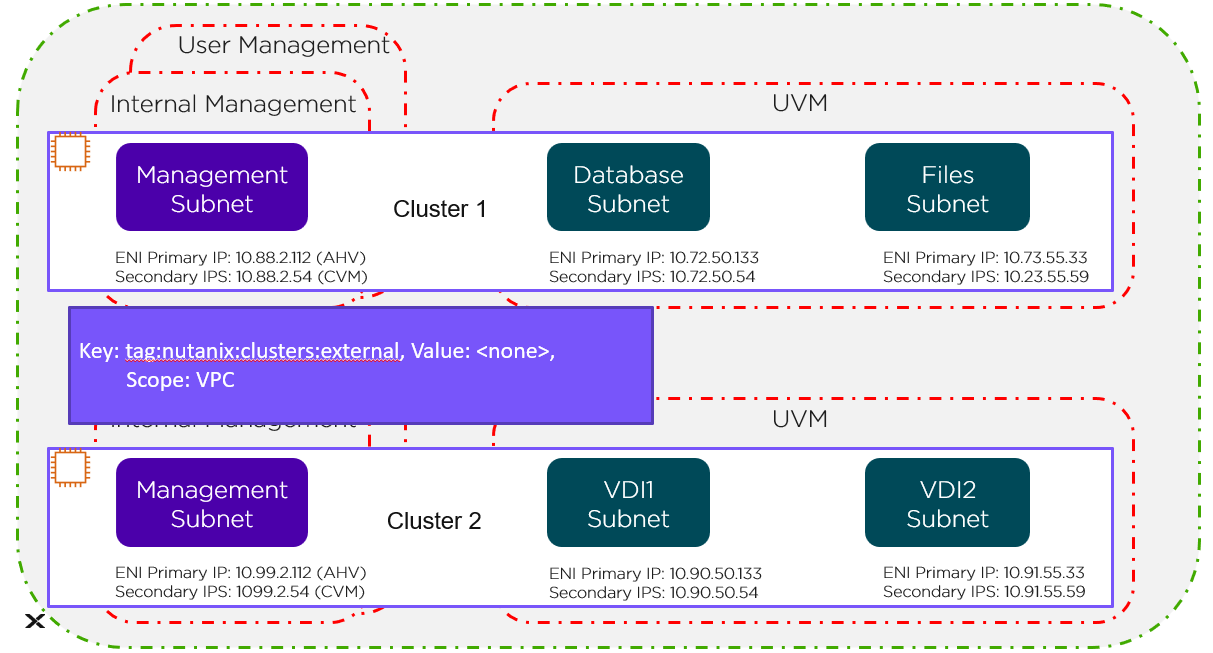
The green line in the preceding figure represents the VPC-level tag protecting Cluster 1 and Cluster 2.
Cluster Level
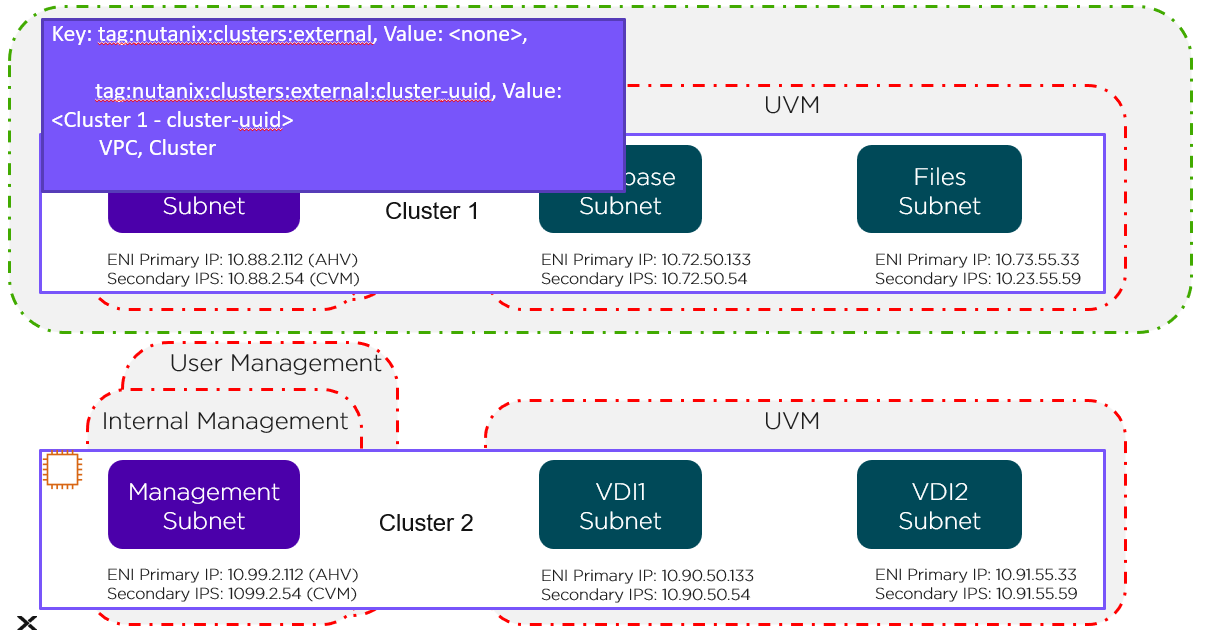
The green line in the preceding figure represents the cluster-level tag. Changes to these Security Groups affect the management subnet and all the UVMs running in Cluster 1.
Network Level
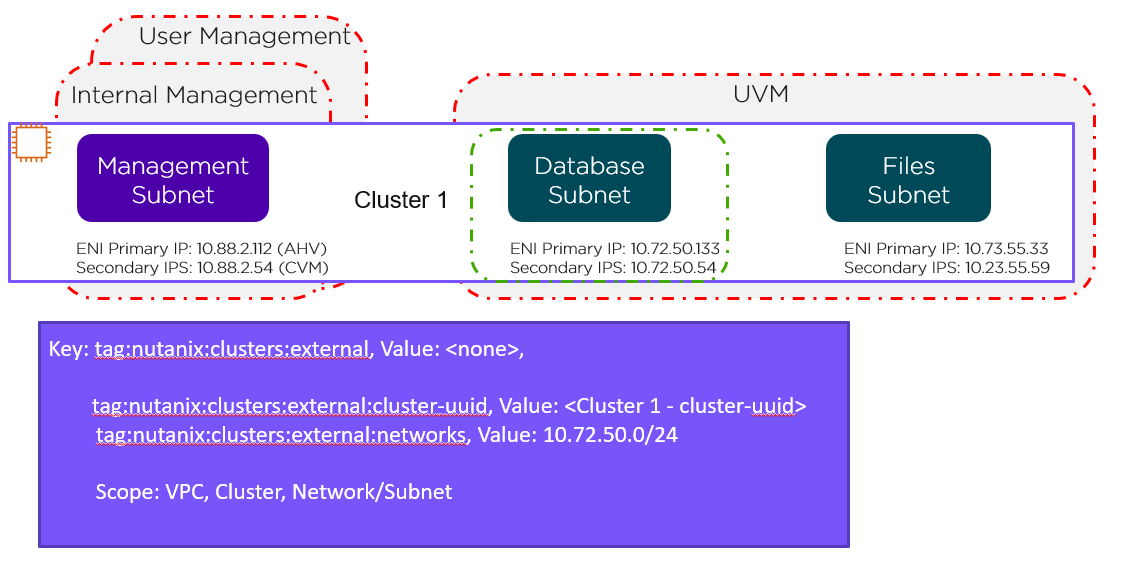
This network-level custom Security Group covers just the database subnet, as shown by the green line in the preceding figure. To cover the Files subnet with this Security Group, simply change the tag as follows:
- tag:nutanix:clusters:external:networks, Value: 10.72.50.0/24, 10.73.55.0/24
These new Custom Security Groups allow the AWS admin to retain control and ensure all workloads have more layers of protection that are consist for all deployments.

