There has been an alarming recurrence of ransomware attacks in recent months across organizations from all industries ranging from healthcare to education. Gartner reports that Twenty-seven percent1 of malware incidents reported in 2020 can be attributed to ransomware.
In a ransomware attack, cybercriminals infiltrate systems using known vulnerabilities and deploy malicious code to encrypt valuable data, holding it hostage until a ransom is paid. By disallowing access to critical business data, these attacks are often more catastrophic than data breaches.
However, with the right preparation, monitoring, and swift mitigation practices in place, ransomware and other sophisticated attacks can be prevented.
Nutanix’s vision is to make security invisible by bringing the same simplicity to security operations that Nutanix delivered to IT operations. We do this by building comprehensive security controls at every layer of the Nutanix® Cloud Platform to help you prevent, detect, and respond to ransomware and other threats. In addition, Nutanix enables defense in depth with a robust ecosystem of security partners.
At our 2021 .NEXT conference we’re announcing that Nutanix will deliver a Qualys® vulnerability management integration with the Nutanix Flow Security Central™ (FSC) solution, currently under development. We are also announcing that a major update to the Security Planning module in Security Central that generates microsegmentation policy recommendations is under development. Security Central is a cloud-hosted SaaS offering that helps Nutanix customers easily assess the overall security posture of their Nutanix deployments and gain the context required to support the implementation of a Zero Trust security strategy in their environments. Additionally, we are extending ransomware protection for Nutanix Files™ storage with the ability to detect and block 4000+ file signatures along with dynamic signature updates through a new cloud-based data governance service, Nutanix Data Lens™.
Ransomware Attack Prevention
Let’s look at the typical ransomware attack chain, where an attacker gains a foothold via a user desktop or a virtual machine due to a phishing exploit, it expands their reach using unrestricted network access within the datacenter, then once the footprint is expanded, it exports and encrypts valuable data.
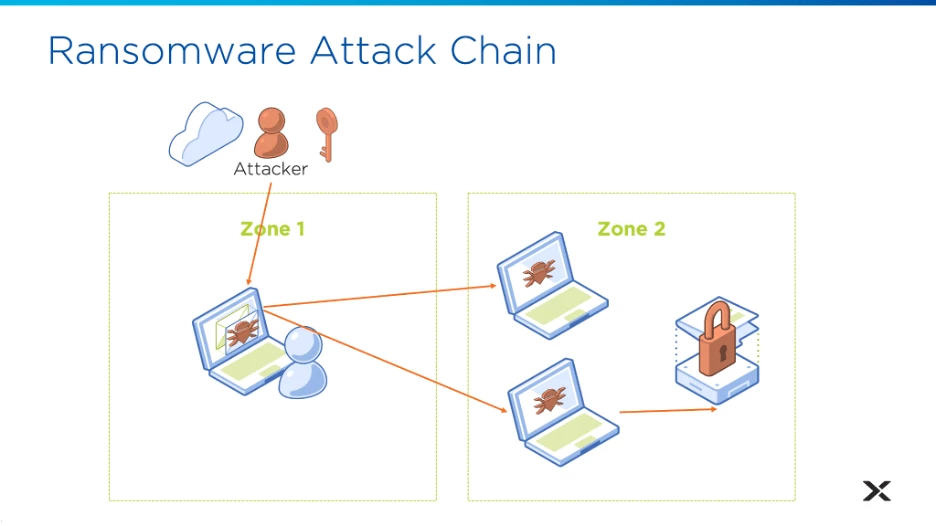
Now let’s look at the weaknesses in each point of the attack chain to see how you would prevent it using Nutanix products.
Continuous Visibility & Monitoring Vulnerabilities
Flow Security Central shows us that this initial foothold machine has a critical, unpatched Microsoft Office vulnerability, using an integration with Qualys’ vulnerability management solution. The security admin is alerted to this vulnerability and stops it before it’s exploited. Flow Security Central also allows you to initiate remediation through ServiceNow® integration or Nutanix X-Play playbooks.
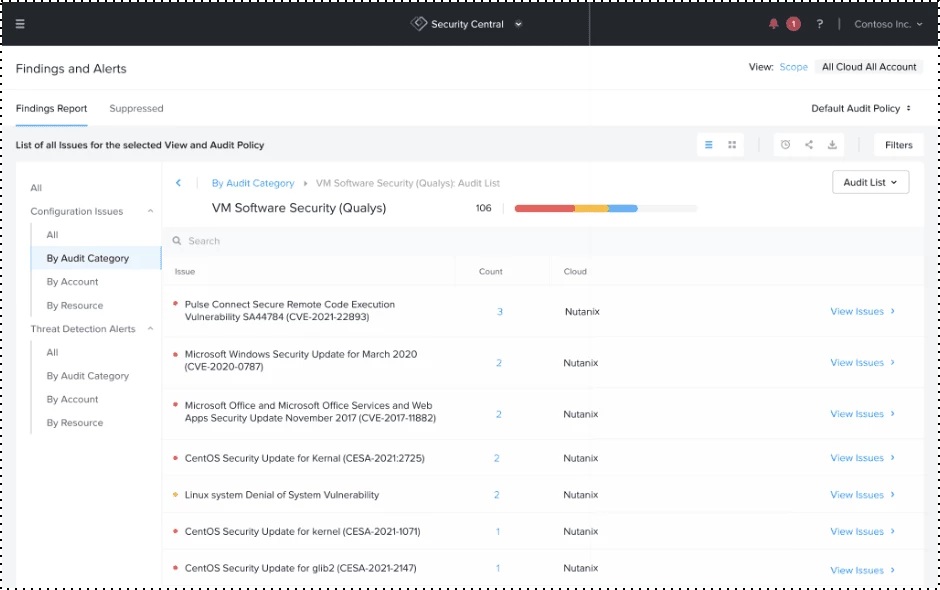
Network Visibility & Security Planning
Additionally, Flow Security Central has ML-based Security Planning to help you to visualize and analyze network traffic, identify VMs, and assign appropriate Categories for which to apply the desired security policy. It also auto-generates the inbound/outbound rules recommendations for the selected set of VMs, ultimately helping you to create a Security Policy that you can apply to your required configurations.
Let’s look at the security planning page for this initial foothold VM in DesktopsZone1.
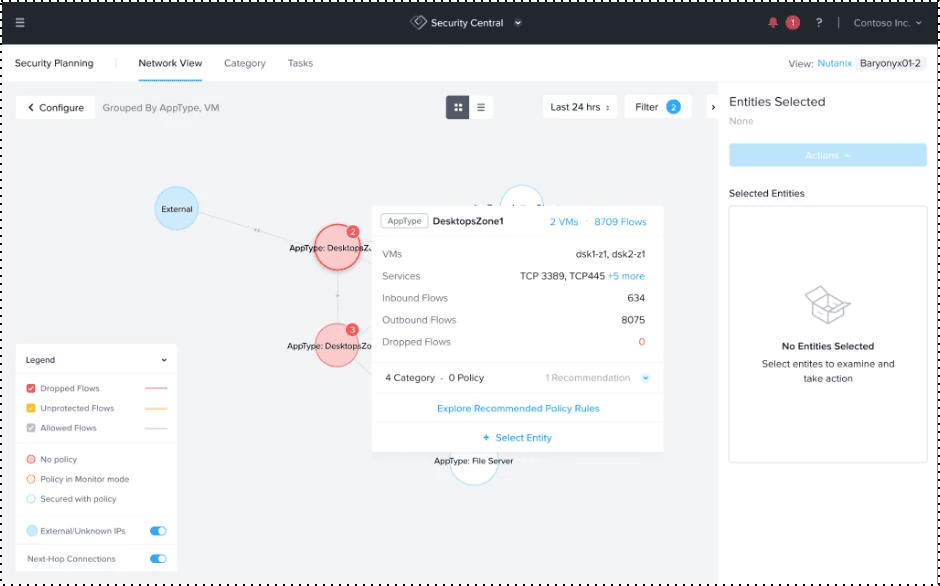
You can identify discovered traffic between the vulnerable desktop and desktop VMs in another zone it should never be able to reach. Using Security Planning, you can apply a microsegmentation policy that stops this traffic spread even if the initial VM was compromised.
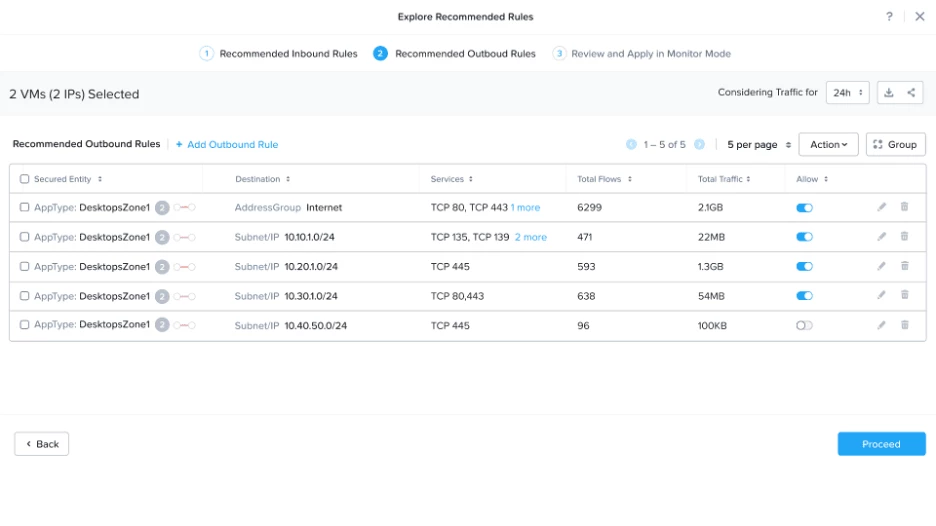
Flow Security Central analyzes traffic over time and generates policy rules recommendations based on learned data.
You can identify traffic that is leaving your protected desktop and going to other desktops. This communication between desktops is a common infection path, so you can block it by unchecking the “Allow” option on these rows. You can then create the Security Policy in monitoring mode, and enforce it from Prism Central to ensure that your secure network configurations are in place to stop these malicious actors from propagating the ransomware infection.
Intelligent Ransomware Block
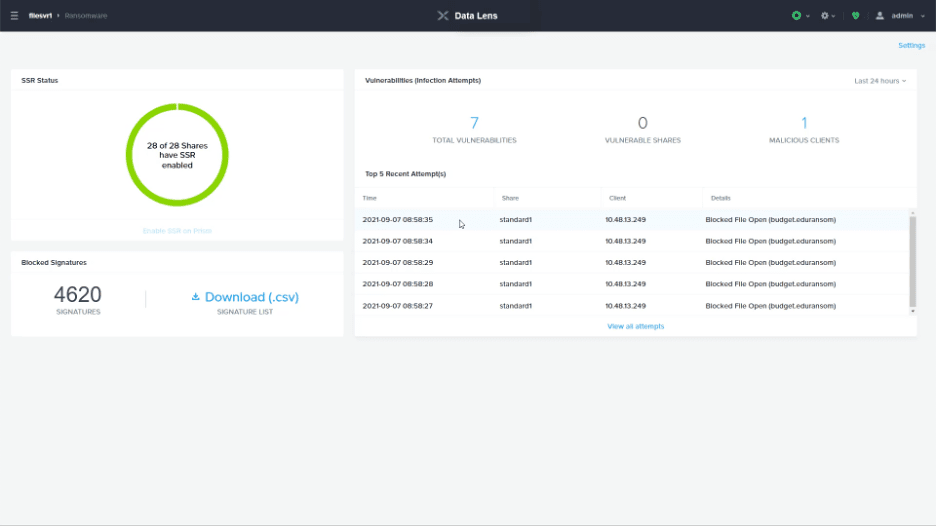
Finally - let’s look at the last step in the process that cripples organizations - where the attacker encrypts business critical files. Using Nutanix Files storage, you can protect this data from being overwritten with built-in capabilities to detect ransomware signatures and automatically block these malicious actions.
Nutanix Data Lens, a new cloud-based data governance service, enables continuous updates of new risk signatures for Nutanix Files deployments. Using the behavioral and data signatures of over 250 different types of ransomware (with more than 4000 signatures under development), Files can detect access patterns and file writes associated with encryption and malicious activity. These activities are blocked so your data is safe, and alerts are generated so the threat can be mitigated.
Conclusion
These are just a few of the tools Nutanix provides for protecting against malicious actors. With these products from Nutanix, you have the tools to help prevent ransomware and other attacks.
With each passing day, cybercriminals are coming up with new and advanced forms of attacks. Vigilance is needed to ensure that IT assets are safeguarded. The key is to have the right preparedness in place that provides continuous visibility and swift remediation.
We are committed to continue with our innovations to help Nutanix customers secure their deployments with confidence. You can look forward to even more functionality in Flow Security Central. We are researching things like network and data activity monitoring, and with Nutanix Data Lens we are applying similar research to detect and protect against anomalous activity at the both of these layers.
Ready to learn more about how to up your security game? Checkout Nutanix Flow, Security Central and Nutanix Files for more information and take a Test Drive today.
This post was authored by Amarkant Singh, Jason Burns, Nutanix
1 [Source https://www.gartner.com/smarterwithgartner/6-ways-to-defend-against-a-ransomware-attack/]
© 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.


