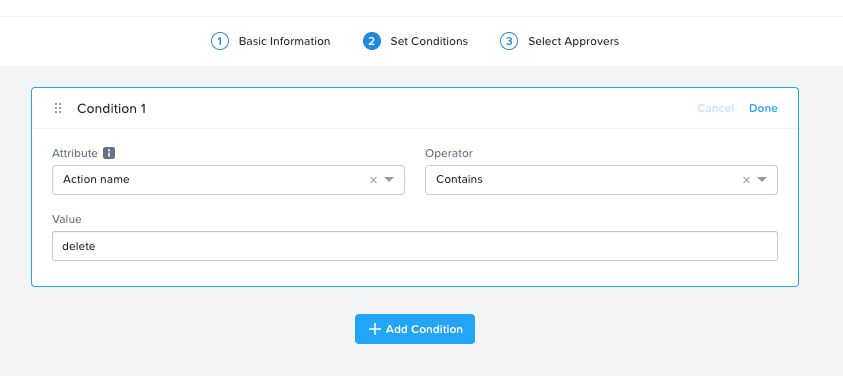
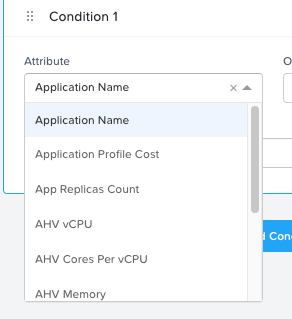
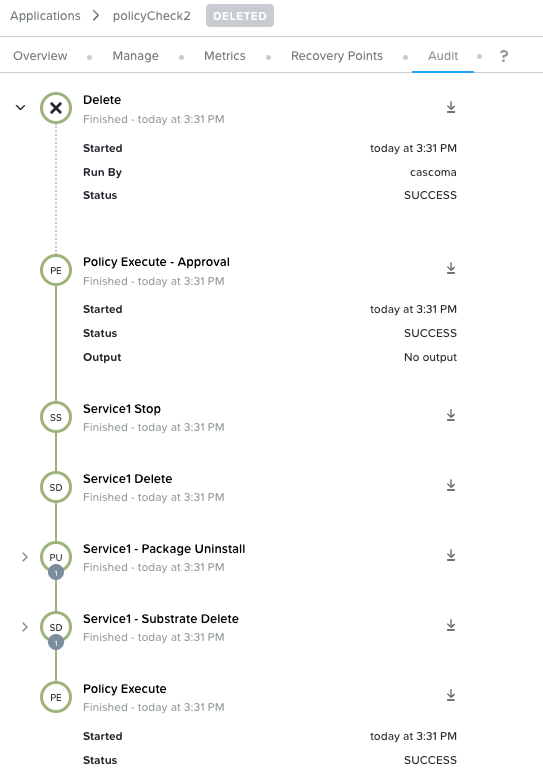
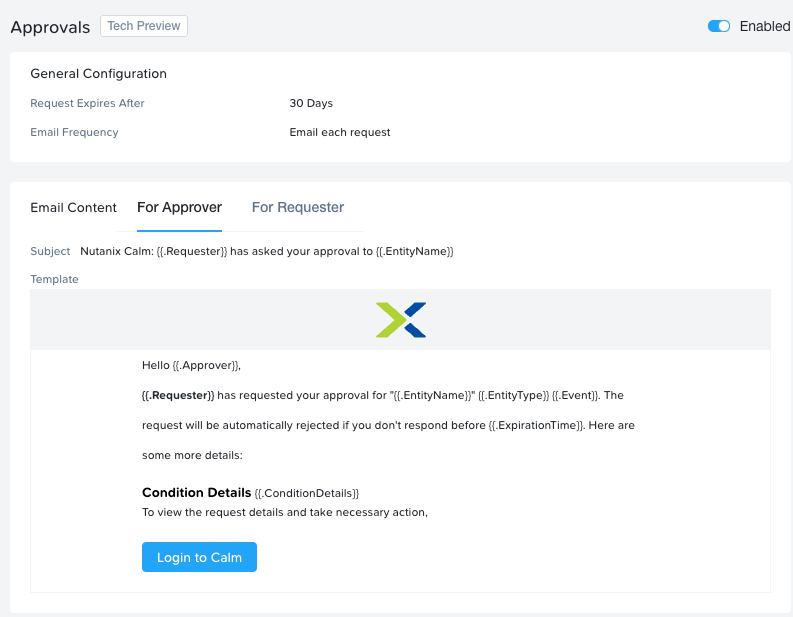
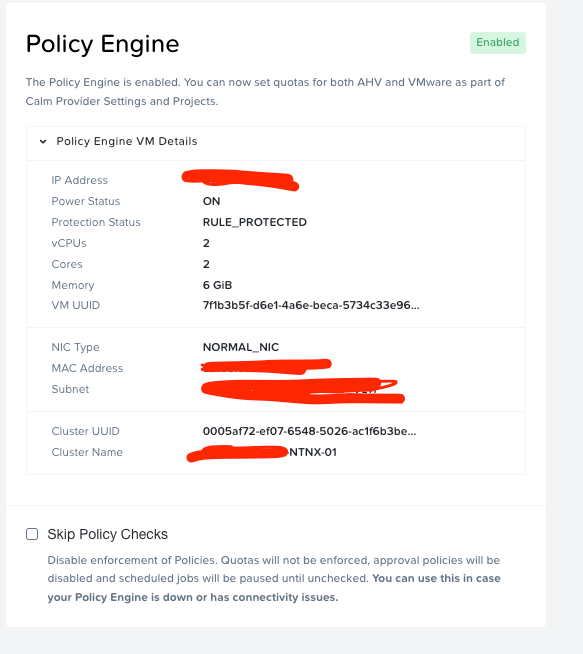
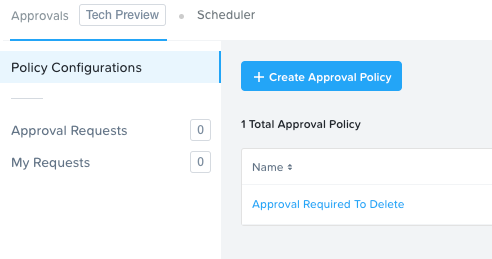
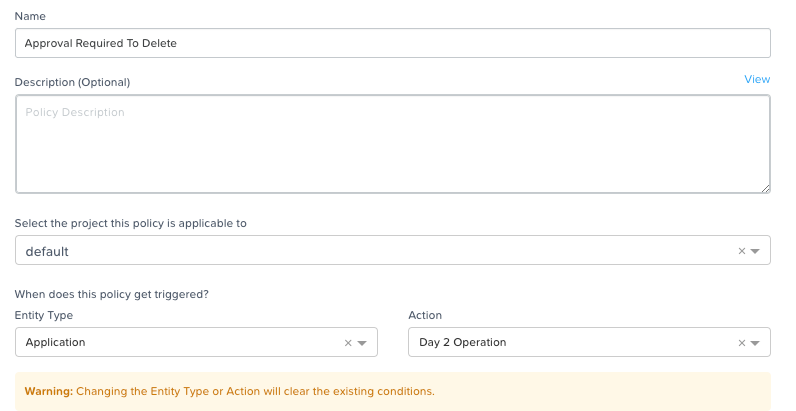
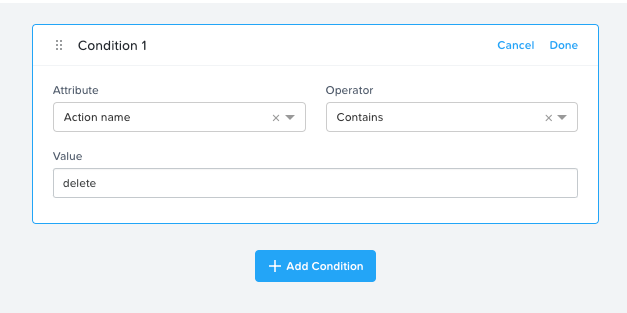
I am looking for a way to protect the VMs that I’ve stood in as Applications in Calm/Self Service from accidental deletion (mostly by me). I don’t see a way to do this in any areas of Prism or Calm, and I don’t see anything in the Policy Manager docs that would address it, either. Is there any kind of pattern or feature for this? Thanks
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.