What is Nutanix Flow?
Nutanix Flow network microsegmentation is a feature in Nutanix’s AHV hypervisor that allows you to control and inspect traffic types across your virtual infrastructure. This is achieved through security policies which can be applied to individual virtual machines or categories of virtual machines. Flow is a function of Nutanix Prism Central and AHV and is enabled with a single-click. As a security best practice, you will want to understand microsegmentation and have a firewall that inspects traffic before you switch this feature on. To use Flow you will need to go to your Prism Central Settings and check to “Enable Microsegmentation” and then click OK.
hypervisor that allows you to control and inspect traffic types across your virtual infrastructure. This is achieved through security policies which can be applied to individual virtual machines or categories of virtual machines. Flow is a function of Nutanix Prism Central and AHV and is enabled with a single-click. As a security best practice, you will want to understand microsegmentation and have a firewall that inspects traffic before you switch this feature on. To use Flow you will need to go to your Prism Central Settings and check to “Enable Microsegmentation” and then click OK.
What is Microsegmentation?
Traditional segmentation works on “north-south” traffic – that is, client-server interactions that cross the security perimeter or a New Generation Firewall (NGFW). Today’s hybrid cloud architectures have changed the way we approach security and network traffic flow. The perimeter now is ignored in most traffic flows, which is because most traffic flows east-west (server to server) between applications. In addition, the proliferation of virtual machines means a single server can host hundreds of workloads, each with its own security requirements. This obviously will require more granular security controls down at the workload level and by combining Nutanix Flow with Palo Alto Networks NGFW VMSeries you are able to monitor and control network activity in your environment.
The following are simple diagrams to illustrate the above points.
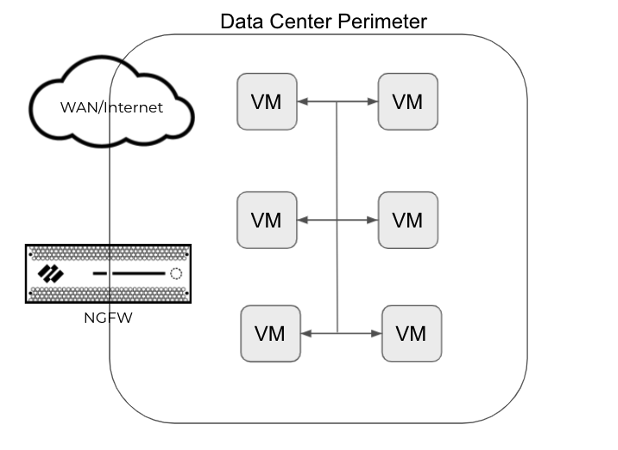
In a traditional network (compared to a microsegmented network) where we would see the flows, a virtualized environment communicates mainly internally. Traffic is localized to mainly east-west between the VM’s. Without monitoring we do not see any unsolicited traffic flows.
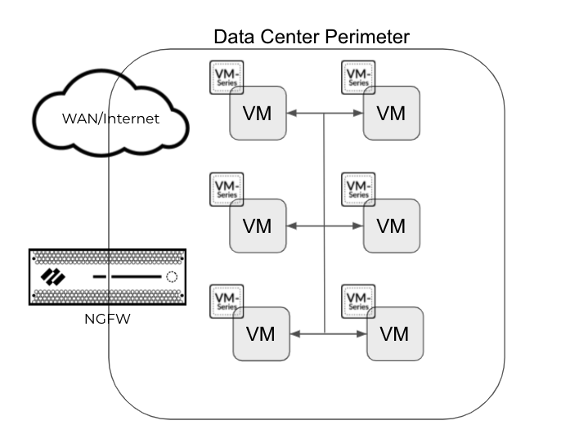
When we implement microsegmentation we can implement a Zero Trust approach with the Palo Alto Network NGFW VMSeries to monitor traffic and allow for only traffic that is meant to flow between the VM’s is directed accordingly using Flow and the firewall.
Why Should you Secure East-West Traffic in your Hypervisor?
Without proper safeguards, attackers can abuse a lack of East-West traffic visibility to move laterally around the network once they get past the perimeter firewall. Threat actors generally move laterally in one of two ways. In the first approach, they scan for open ports that are listening as well as machines that suffer from known security vulnerabilities. This is where Nutanix Flow and the Palo Alto Networks NGFW VMSeries can really help, as this sort of traffic would be immediately blocked. If there are no safeguards in place an actor could try to abuse the found weaknesses to move laterally within the hypervisor’s network.
The second method of lateral movement, is that an attacker may use a phishing email to infect a machine via an administrator account with a keylogger or another type of information stealer. This malware secretly collects credentials entered by the user on the infected machine and sends this data to the attackers. At this point, the threat actors leverage these details to impersonate the victimized user and authenticate themselves on legitimate services. Again with Nutanix Flow and Palo Alto Networks NGFW VMSeries, this type of attack would immediately be seen and blocked, no data would be transmitted outside as the policies and zone trusts implemented would prevent this. Information collected by these threat actors from these types of attacks forms the basis for their ability to move laterally to other parts of the network so that they can compromise the intellectual property and/or customer data of their target.
In Summary
Microsegmentation is an important element in your total security posture as a company and as an IT department. It’s important to realize that the features covered here are not a quick fix or a simple implementation. This should be part of a bigger picture approach with your Zero Trust model adopted by your organization. Controlling your network flows at the application work level requires a consultative approach to achieve the outcome of a listed and understood environment. Also once you have finally implemented the controls mentioned above you will be well on your way to having a well managed and secure environment.
This guest post was authored by Steven Riley, Palo Alto Networks
 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.


