https://next.nutanix.com/how-it-works-22/network-segmentation-basics-38414
It seems the network segmentation 2.1 doesn’t support the isolation physically between the backplane and management.
So, it tries to isolate logically following this procedure.
ISOLATING THE BACKPLANE TRAFFIC LOGICALLY ON AN EXISTING CLUSTER (VLAN-BASED SEGMENTATION ONLY)
https://portal.nutanix.com/page/documents/details?targetId=Nutanix-Security-Guide-v5_15:wc-network-segment-on-existing-cluster-wc-t.html
AOS5.15.1 / ESXi 6.7u3
Standard vSwitch, vSwitch0
Port Gourp: Backplane Network, CVM Backplane Network (for CVM)
it doesn’t recognize any port groups.
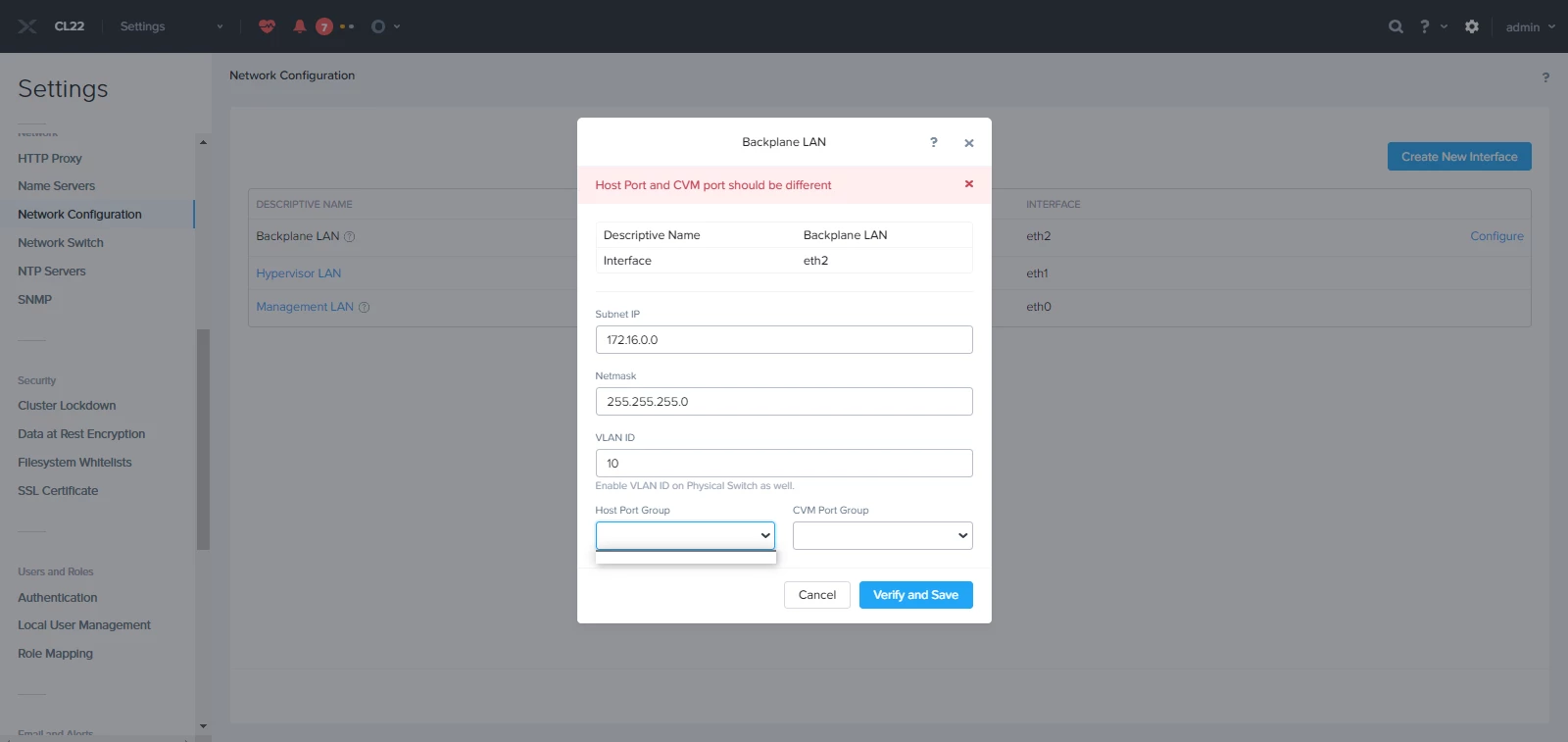
The procedure doesn’t mention about the vSwitch0 or port group condition.
Is there any information of this?
Thx,
Best answer by lk541
View original


