This post was authored by Neil Ashworth Security Solutions Architect Nutanix
What is it?
Viruses, Malware, Spyware, Adware, Phishing, Vishing, Worms, Trojans, Infections, Exploits, Vulnerabilities, Hackers, and Crackers. An industry with such confusing terminology can be naturally repellent to many in I.T. especially those outside of infosec. Commonplace security terms can all sound a bit like gobbledygook and confusion leads to frustration and then in many cases to indifference. Even for those in the Security field, it can be difficult to keep abreast of the latest exploitation trends, but to almost everyone in the I.T. industry, Ransomware is a term known to all, a threat so ubiquitous it commands attention from even the most infosec apathetic of system administrators.
There are many threats that exist in the digital age, where skilled digital opportunists lurking in darkened coffee shop corners, most likely wearing hoodies, laughing sinisterly over a small cupped espresso, poised and ready to take advantage of holes or “exploits” that might exist in your digital environment.
Ransomware is a highly profitable method used by these cybercriminals, with an aim to disrupt normal operations in an organization (or against an individual) to the extent that the affected party might be willing to pay for the chance to get back to a normal system state. A layman's description of Ransomware is simply that Cybercriminals block access to your data and hold it ransom.
It works as malicious software (malware) which gains a foothold into the environment possibly via phishing or spear phishing emails or by unknowingly visiting an infected website. Ransomware over the years has manifested itself in different forms an evolution of sinister intent, and has different severity levels ranging from mildly infuriating to a Chernobyl level event!
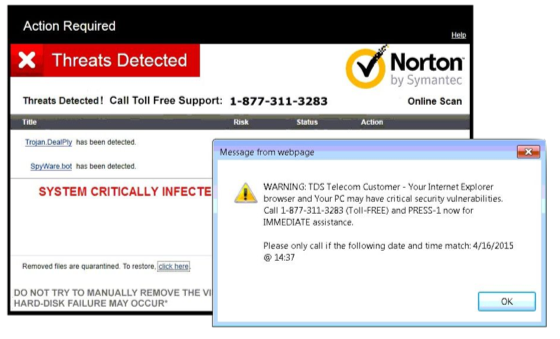
Scareware - This is just smoke and mirrors. Theatrics, designed to trick the end user into downloading something potentially much more dangerous and destructive. This is sometimes the entry point for viruses, worms, encrypting malware or remote connectivity.
Screen lockers - These are more severe, kind of scary, and more difficult to remediate. A lock screen prevents you from being able to view anything on your machine and is often designed and worded in such a way that makes you believe the FBI or other legal authority has locked you out to perform “analysis” on your machine. Rest assured even if your activity was slightly dubious police and government are not in the business of alerting criminals by locking them out of their own property.
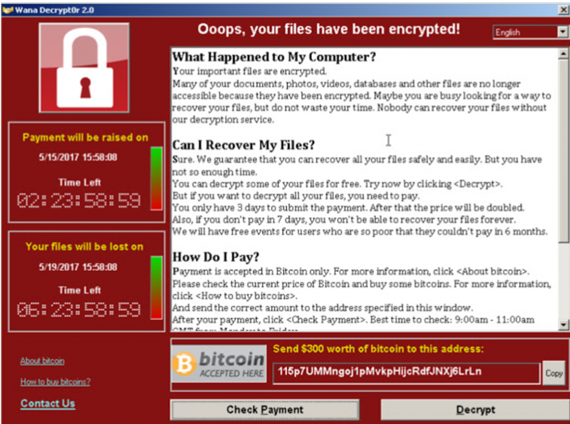
Encrypting Ransomware - Chernobyl time. Files are identified and encrypted with the keys used in encryption stored on a remote server. A message from the attacker is displayed informing you of the encryption and demanding payment for those files to be decrypted. This is uniquely dangerous because once a cybercriminal has control of these files no security software or system restore can get that access back. The only options available are to pay the ransom or restore from a backup. The most infamous version of this was the WannaCry crypto-worm which targeted Windows back in 2017 and still impacts companies and organizations today.
Case study and statistics
As recently as March of 2019, one of the largest beverage suppliers in the U.S. (let’s call them AZ Beverages) were subjected to a suspected iEncrypt ransomware attack. The message “Your network was hacked and encrypted” appeared across the monitors of over 200 servers and computers on the network. The company decided not to pay the ransom as they had a backup solution from which they could recover from. Unfortunately for them, the configuration of this backup (which turned out to be old and unpatched) led to failures to recover and subsequent delays, costing hundreds of thousands of dollars.
This isn’t an isolated incident:
- A new organization will fall victim to ransomware every 14 seconds in 2019, and every 11 seconds by 2021. (Source: CyberSecurity Ventures)
- 1.5 million new phishing sites are created every month. (Source: webroot.com)
- Ransomware delivered by 97% of phishing emails - BOOMING cybercrime industry (Source: Cofense)
- A total of 850.97 million ransomware infections were detected by the institute in 2018.
- 34% of businesses hit with malware took a week or more to regain access to their data. (Source: Kaspersky)
- In 2019 ransomware from phishing emails increased 109 percent over 2017. (Source: PhishMe)
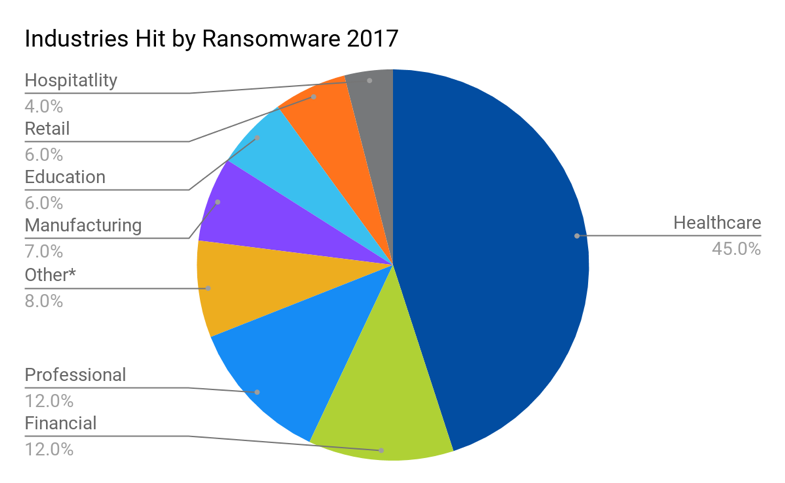
2017 Ransomware incidents by industry [1,2]
Front-line defense strategies?
Typical best practices around protecting your digital environment remain relevant when attempting to defend against Ransomware attacks. Without them you’re asking to be compromised; with them you might make the journey to exploitation slightly more arduous and therefore less attractive to less sophisticated hackers.
By best practices we mean those suggested actions to be taken by security engineers which are generally agreed to be a good starting point with which to protect organizational I.T. such as endpoints, computer systems, data center and cloud infrastructure etc. Examples of such actions are:
- Use network isolation/ segmentation for workloads, departments, between applications and databases, and definitely around your most sensitive data.
- Use and maintain endpoint protection/ antivirus agents to block payloads from launching.
- Use Intrusion Detection and Prevention systems (IDS/ IPS) to identify potential sprawl of malware.
- Train your employees, regularly! Your first line of defense is a well educated front line.
- Restrict access to sensitive systems, authenticate and authorize not just people but services.
- Patch Systems regularly. (OSs, Hypervisors, Firmware, BIOSs etc).
- Change ALL default passwords, enforce strong password policies and rotate them frequently.
- Scan regularly for Common Vulnerabilities and Exposures (CVEs).
- When using Public cloud, follow recommended hardening guidelines and restrict access to those accounts strictly.
- Think about your blind spot; printers, telephony, peripherals. Lock them down and lock them out
I could go on but ultimately the point is that using various tools and systems in partnership with one another are key front-line defense strategies against the potential of compromise.
All of that, unfortunately, might not be enough. Nutanix uniquely uses additional methods to harden our environment from possible compromise. Nutanix, for example, baselines and hardens AOS and AHV based on Security Technical Implementation Guides (STIGs) and self-heals deviations from this IA baseline with built-in Security Configuration Management Automation (SCMA), but again these in of themselves aren’t solely a means to successfully defend against Ransomware.
MSPs (Managed Service Providers) rank BCDR (Business Continuity & Disaster Recovery) solutions as the most effective solution for Ransomware protection compared to other solutions.
The takeaway from this is that ransomware attacks will inevitably happen, to protect clients and effectively respond to attacks BCDR is crucial to prevent downtime[3].
With BCDR, 90% of MSPs report clients fully recovered from an attack within 24hrs or less
So, a full, rounded solution forms part of your anti-ransomware strategy, but that won’t always be enough. Establishing and maintaining a robust, repeatable and frequently tested backup/ recovery method is the fastest way to heal from a ransomware incident, but before we jump into how to recover from a ransomware event, let us quickly look at one further tool available to Nutanix customers that aids in the prevention of lateral movement (spreading) for malware such as ransomware in your data center.
Nutanix Flow
If we were to imagine what an organization's potential security process might be with Nutanix and our suite of products, from the moment an infected machine becomes identified, it might follow a process similar to what is outlined below.
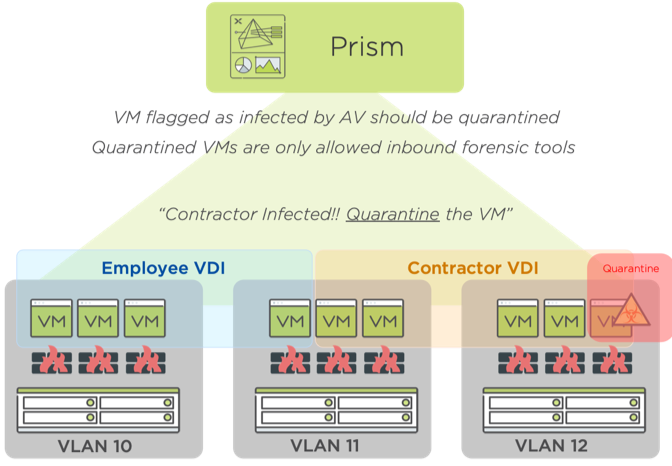
Third-party Endpoint protection tools can identify suspected/ anomalous activity on a given VM, or the end user(s) can raise the issue with the organizations Security Team. Nutanix Flow allows for micro-segmentation of the virtual environment and in this situation, a “Quarantine Policy” can be imposed on the infected VM(s) by the Security Engineers or automated via integration with threat detection software (SEIM, IPS, AV, etc). Now that the machine is isolated and the spread contained, root cause analysis, forensics, and notification of the authorities can begin.
Once all analysis has been completed the machine can be easily destroyed and rebuilt. One point to note here is; since ransomware crypto-worms seek out methods by which to spread themselves to other connected systems, either via open obscure ports, and protocols like RDP. Flow assists further in their confinement even before a Quarantine Policy has to be activated, by blocking all non-permissible traffic as part of established Application level policies. Identification of suspect traffic by network or security engineers is also highly visible in the Prism Central Flow visualization dashboard.
Get back to work!
The data that is likely unrecoverable from the infected machines could have also been protected by Data backup and BCDR. Nutanix uses a VM based Protection Policy when creating snapshots from which to recover VM’s. These Protection Policies can be set by Categories (a metadata grouping mechanism) as well as specifically calling out individual VM’s. Categories help keep policies like this fresh and flexible to the dynamic nature of cloud computing. Once the security team has identified the point and time of the malware ingress we have a safe point with which to try and recover from, locally or remotely retained snapshots give customers flexibility in recovery points.
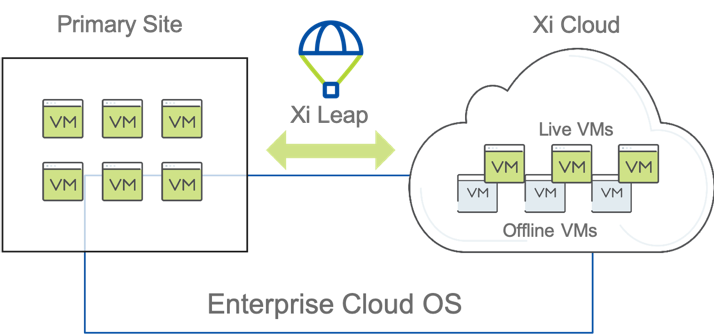
Xi Leap
As we’ve previously discussed, the fastest way to achieve normal operations currently, is with Business Continuity and Disaster Recovery (BCDR). Xi Leap is an Enterprise ready Disaster Recovery solution which can support your entire Nutanix Private Cloud. Xi Leap’s DRaaS (Disaster Recovery as a Service) offering integrates seamlessly into your existing Nutanix footprint and begins replication as soon as connectivity is established and Protection Policies are set.
With a simple setup process, applications can be replicated to one of Nutanix’s Availability Zones (AZ) located on the East and West coasts of the U.S. and in London, England[4]. Once a Protection policy and Recovery plan are established data immediately begins seeding the recovery site.
With RPO (Recovery Point Objectives) available as low as 1hr, backed up by SLA (Service Level Agreements) by Nutanix, and Recovery Time Objects (RTO) to match, impact to the business can be kept to a minimum. Xi Leap can turn a nightmare Chernobyl scenario into a slight annoyance, or support Business Critical Operations in the cloud until the situation at the private DC is fixed.
If full Disaster Recovery and the running of live VM’s in a remote cloud site, while you remediate your private DC isn’t necessary, Nutanix and our partners can provide other solutions.
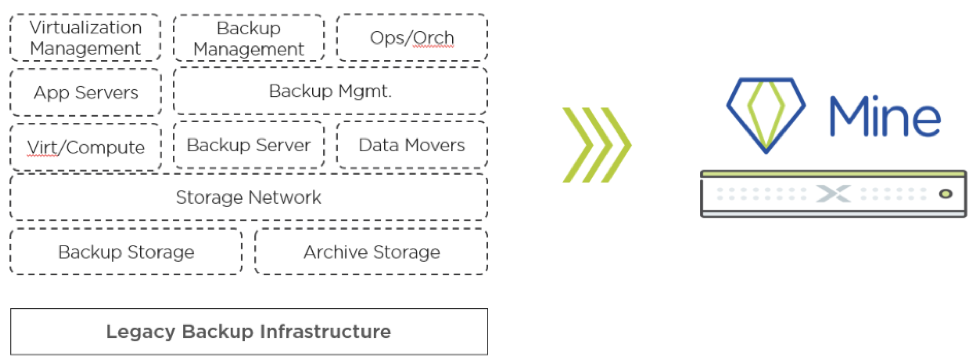
Nutanix Mine
For organizations that are interested in Data Protection over Disaster Recovery, those that can potentially accommodate a downtime to purge the malware from their private data center, and have a secondary location to set up a Data Protection site, we have Nutanix Mine.
Nutanix Mine is an integrated Data Protection solution that leverages the strengths of the Nutanix core AOS software that we’ve built over the past 10 years. It integrates with data protection software from Veeam and HYCU, so their software runs in a hyper-converged manner on the appliance itself.
All the immense complexity that is used in configuring traditional methods of data protection are eliminated on Nutanix Mine. Remember the case study from earlier about our AZ Beverage company, and their failure to recover data quickly because of significant issues with their backup solution? Imagine the peace of mind that can be felt from knowing that you’re protected and ready to recover at a moments notice on a tried and tested modern Data Protection solution.
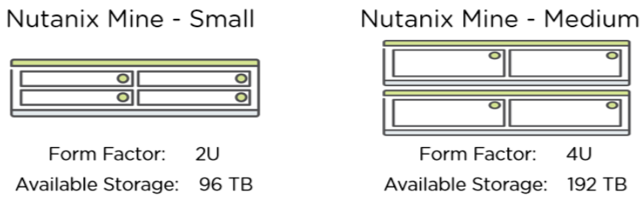
Nutanix Mine is available in two easy-to-size models, and includes the Nutanix licenses:
The Small form factor is based on the NX-1465-G6 platform, the Medium uses 2 NX-8235-G6 enclosures. Expanded line-ups with other hardware platforms to be added in the latter half of 2019.
Furthermore, if your organization has regulatory requirements to keep your backups for an even longer period of time, you can tier off the backups to another tier of storage. This tiering is done using the backup software to convert the backups into objects and store them onto an S3 compatible location. This can either be a cloud-based offering like AWS S3, or something in your own datacenter, like a Nutanix Buckets cluster.
Partner Solutions
One of the reasons customers love Nutanix as much as they do is our commitment to creating and maintaining an open platform. There are going to be different solutions that appeal to, or are a better fit for different customer workloads and requirements. We have long understood and embraced this diversity and are proud to accommodate a multitude of services from our Alliance Partnerships.
HYCU
HYCU is Data protection designed for Hyperconverged Infrastructure. A purpose built application and data protection solution for Nutanix. Not only does it preserve HCI simplicity with native integration and hypervisor-agnostic architecture that includes AHV and ESX, but it also makes fully reliable backup and recovery a sure thing.
Veeam
Veeam is a leader in Cloud Data Management and a key Nutanix partner. Cloud, multi-cloud, on-premises, virtual and physical servers: Veeam solutions Backup, replicate, and enable cloud mobility. In addition, Veeam offers broad data management and visibility/control capabilities and an extensive orchestration engine to facilitate disaster recovery (DR) readiness. Veeam platform provides customers Agility, Availability and Business Acceleration.
Commvault
Protecting a Virtual Machine (VM) might seem simple. Protecting thousands of virtual machines — each with differing requirements for protection, recovery, reporting, and Disaster Recovery (DR) — is not so simple. Commvault can help simplify managing these complex challenges using SLA-based protection plans, to ensure that each virtual machine is managed exactly as your business requires.
Veritas
“With the combined power of Nutanix and Veritas that blends a leader in hyperconverged infrastructure (HCI) and Enterprise Cloud with the premier backup and recovery solution on the planet, customers can now protect a vast array of enterprise workloads” - Rama Kolappan VP Product Management & Alliances, Veritas.
For more details on these great products please contact your local Nutanix or preferred Data recovery solution representative.
Closing thoughts
If you’ve kept with me this far, congratulations! And, if you’ve found these ramblings of a mad man slightly anti-climatic, “I thought you could tell me that Nutanix is ransomware proof!!” then I can only apologize. My hope is that you are encouraged by what you’ve read thus far, granted no one solution in isolation is the silver bullet to this bane of the computer age, but Nutanix can drastically simplify the process of protecting infrastructure and implementing a recovery solution which will, in turn, improve the operational cost of resuming business operations without having to pay a costly ransom. Nutanix is intrinsically secure, providing solutions to help prevent the possibility of malware lateral movement and setting a path to quick remediation capabilities.
Unfortunately, ransomware is an effective money machine for those black-hat cybercriminals, and as long as companies continue to pay the ransom, many of which do simply because their recovery strategy either doesn’t exist or isn’t easily implemented, these tactics will continue.
TLDR; My “personal” top 3 tips for combating ransomware attacks are:
- Backup your data! Regularly and retain a decent[5] amount of snapshots. By far the most powerful strategy to combat Ransomware.
- Train your employees in spotting phishing, spear-phishing and vishing (voicemail deception).
- Lock it down. Zero trust. Don’t rely on perimeter protections only, use Flow to keep it simple.
To learn more about how Nutanix can help with your ransomware defense strategy, check out our Ransomware Threat Tech Brief.
 2019 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and the other Nutanix products and features mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s).
2019 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and the other Nutanix products and features mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s).
----
[1] Other includes utilities, construction, government, and real estate
[2] Source: BBR Services 2017
[3] Data obtained from datto.com 2018 State of the channel ransomware report
[4] Locations are correct at the time of writing, however additional AZs are being established in Italy, Germany, Japan. Contact a Nutanix Xi Leap rep for further details
[5] Decent is entirely subjective to your own environment